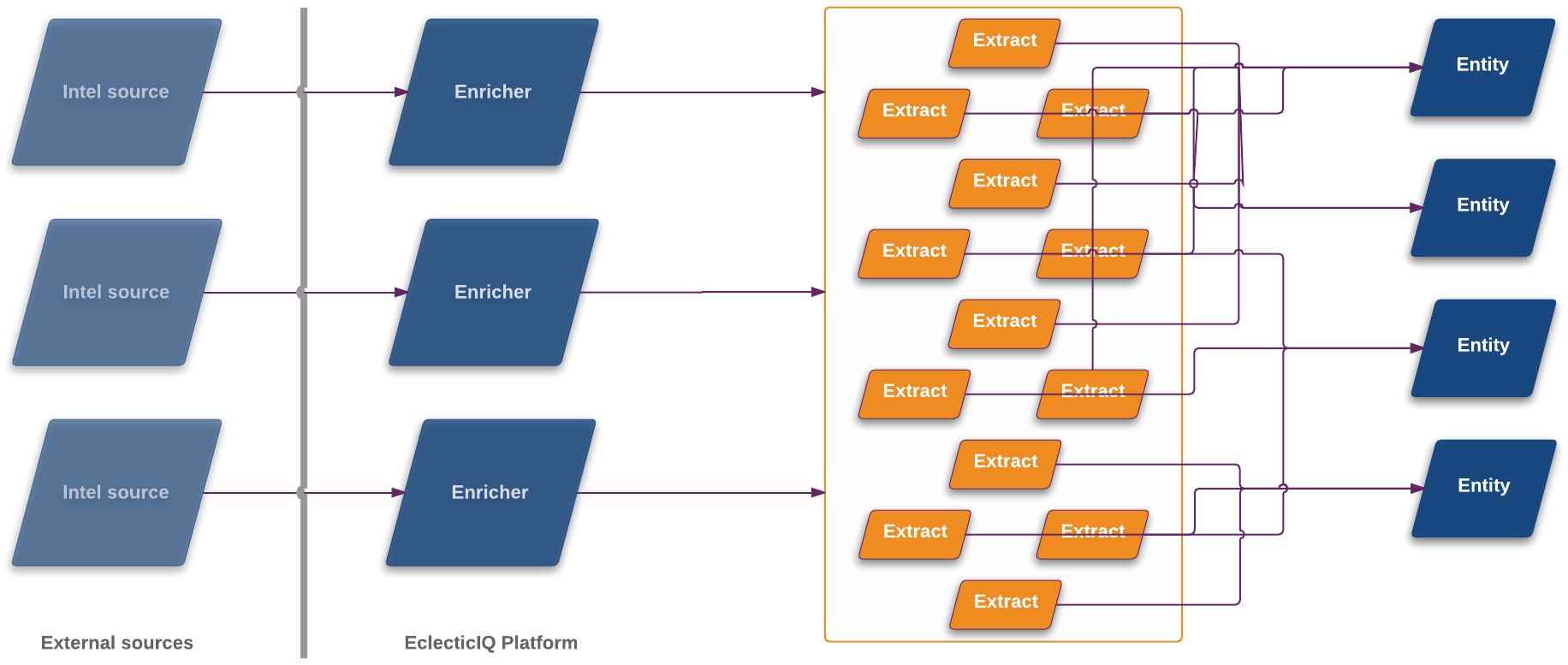
About enrichers#
Enrichment augments existing cyber threat intelligence value by adding contextual information. Enrichers use rules and tasks to automatically enrich entities, so that you can explore a broader and more granular cyber threat intelligence landscape.
The platform can ingest cyber threat intelligence through incoming feeds, by manually uploading one or more files, or by creating an entity in the entity editor.
After ingesting and saving entities to the database, you can integrate the existing information with additional details. The extra information is raw data that augments the entity intelligence value by adding more context and meaning to it. The data is extracted from different sources such as feeds, reports, database searches, curated intel distribution lists, and so on.
The platform uses enrichers to fetch and extract the data. Enricher rules sift through the data to link it to relevant entities as Enrichment observables. This process does not alter core entity data: each bit of enriching information is saved to observables, which are related to entities.
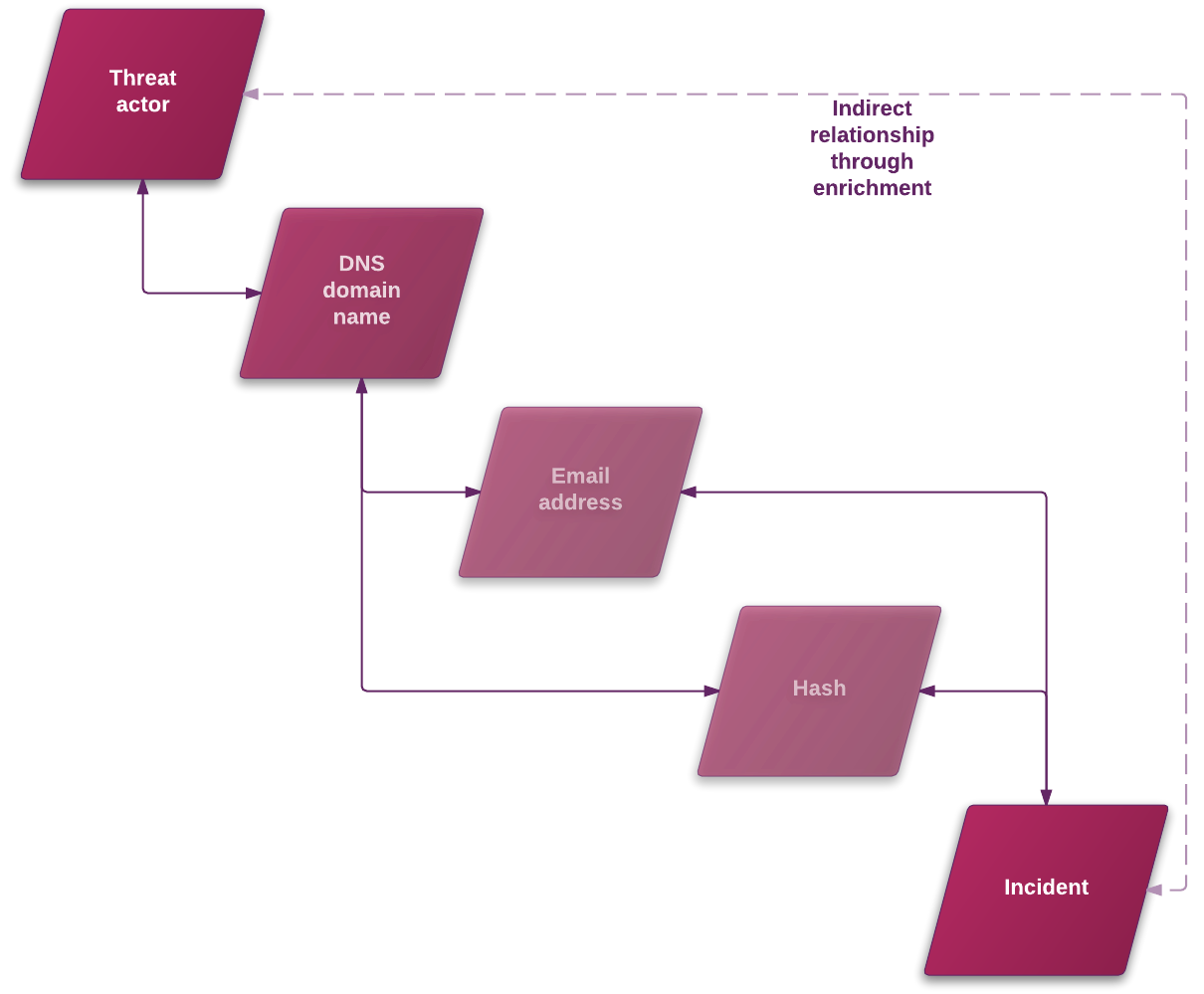
For example, let’s assume a scenario where an analyst is investigating a threat actor entity. The entity includes some observables, and one of them is a DNS domain name.
The analyst looks up the domain name by running it through a whois service. The lookup results include an email address.
During the investigation, the analyst also retrieves a file hash related to the domain name.
An examination reveals that the hash is related to an incident. Information about the incident includes the same email address detail the DNS domain name returned.
There is an indirect relationship between the threat actor and the incident that would not have been noticeable without extra context, which in this example is provided by the hash.
Enrichments help get a broader and sharper picture: by adding meaningful context, they help discover broader, indirect relationships that are not immediately visible.
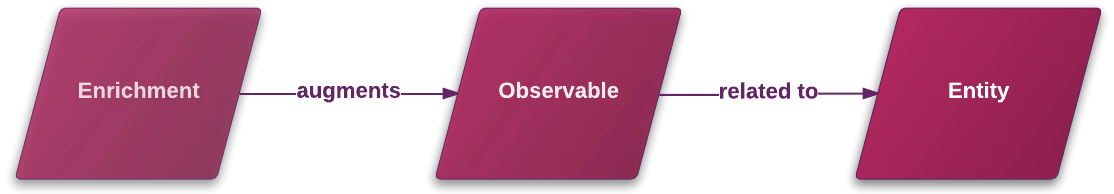
Enrichments augment observables with raw data information related to entities:
About Enrichment and filtering#
Data extraction produces observables from data retrieved in embedded CybOX objects.
This process contribute to data fusion across the whole platform dataset.
Enrichment rules sift through data to augment it with Enrichment observables, that is, observables obtained from the available Enrichment data sources, and to exclude specific data based on the defined filtering rules.
You can further refine the quality of the extracted data by applying ad-hoc rules to classify observables as safe or malicious.
STIX and CybOX objects can both
include placeholder references to external
objects and data in the idref field.
By default, the platform
attempts to resolve idrefs at entity level and at nested object
level by looking for the actual data the idref value represents
and refers to.
If it finds matching data, it creates either a
relationship between entities — entity-level, STIX idref
resolution — or it replaces the idref placeholder value with
the corresponding actual data — nested object-level, CybOX
idref resolution.
About Enrichment and maliciousness#
When an Enrichment provider makes available ranking or scoring information, enrichers use this data it to calculate Enrichment observable maliciousness level.
The minimum maliciousness level an enricher can assign to an Enrichment observable is Malicious - Low confidence.
To mark specific observables - including Enrichment observables - as safe or eligible to be ignored, create observable rules whose Action is either Mark as safe or Ignore, respectively.
About Enrichment rules and Enrichment tasks#
Enrichment rules and Enrichment tasks drive the Enrichment process to:
Poll selected and trustworthy intelligence data sources;
Retrieve relevant, accurate, and reliable data to augment platform entities with extra bits of information that provide additional context.
Enrichment rules#
Enrichment rules define what to do with the retrieved Enrichment data. Rules act like filters, and they set the logical constraints defining:
The platform data sources to augment with Enrichment information.
Data sources you can enrich are incoming feeds, other enrichers, and groups.
Within the selected platform data sources, the entity type(s) to augment with Enrichment information.
The enrichers to use to fetch Enrichment data.
Enrichment tasks#
Enrichment tasks define process execution by setting the following options:
The data fetching mechanism.
For example, an API endpoint exposing the Enrichment data service.
Specific data sources
For example, datasets targeting threat actors like hackers and terrorist groups.
Data rate limit and monthly execution cap values to control the amount of polled data.
A source reliability flag for the incoming Enrichment data to simplify assessing the quality of the retrieved data.