EIQ-2021-0006#
ID |
EIQ-2021-0006 |
|---|---|
CVE |
- |
Description |
SVG file upload could allow cross-site scripting (XSS) |
Date |
28 Jan 2021 |
Severity |
2 - MEDIUM |
CVSSv3 score |
CVSSv3 score not available on NIST NVD. |
Status |
✅ 2.9.2 |
Assessment |
It is possible to manually upload to a workspace an SVG file that can inject malicious JavaScript upon rendering the uploaded file. This could enable exploiting the vulnerability to carry out a cross-site scripting attack (XSS). To exploit the vulnerability, a potential attacker would need to:
By opening the Therefore, embedded JavaScript code in the SVG file can access the token, and use it to send valid requests to the platform API. A signed-in user without admin access rights could exploit the vulnerability if they have at least the permissions to access and modify workspaces, as well as upload files to workspaces:
Proof of concept Uploading a crafted SVG file with embedded JavaScript such as the one in the example, and then rendering it as a preview through the <?xml version="1.0" encoding="UTF-8"?>
<svg id="Capa_1" xmlns="http://www.w3.org/2000/svg">
<script>alert(1)</script>
</svg>
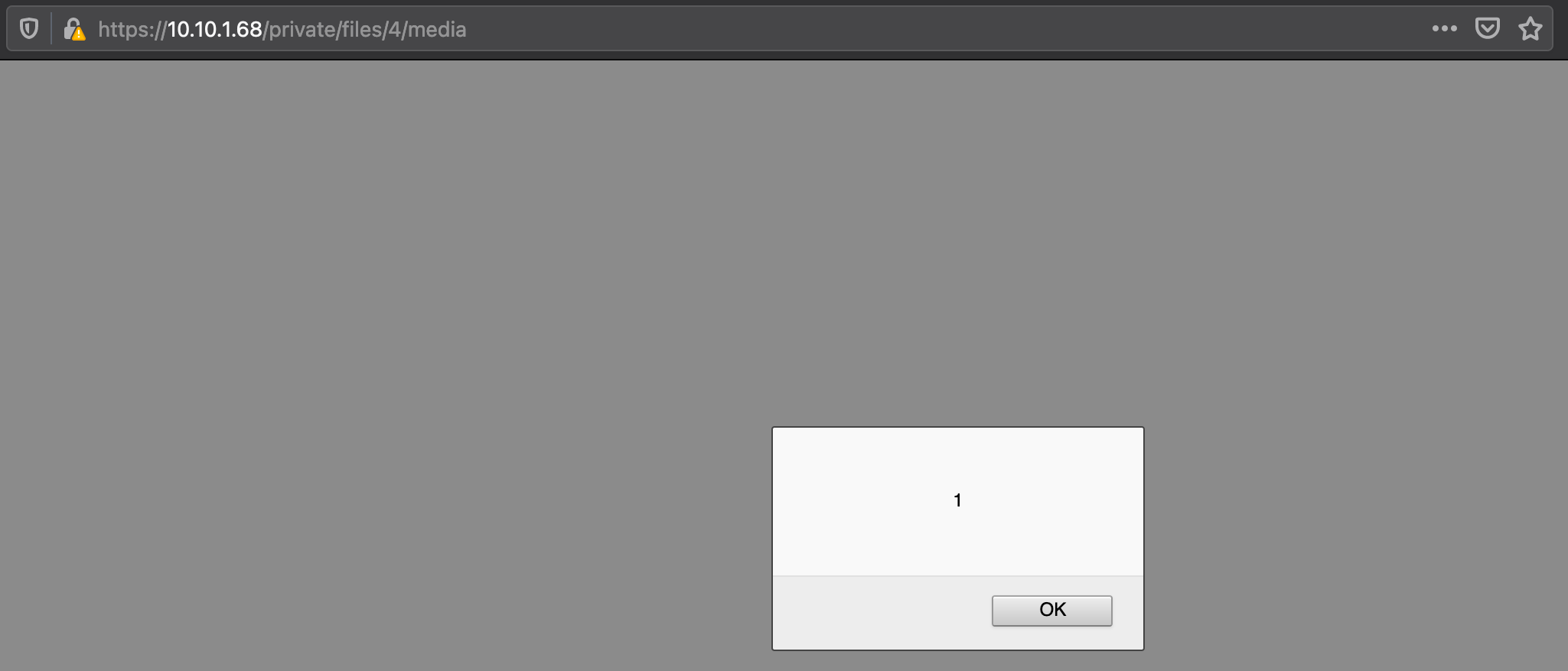
XSS through JavaScript embedded in an SVG file uploaded to a workspace.# |
Mitigation |
This vulnerability is addressed in EclecticIQ Platform 2.10.0 by applying stricter XML sanitization, and by deprecating the |
Affected versions |
2.9.1 and earlier. |
Notes |
n.a. |