EIQ-2021-0005#
ID |
EIQ-2021-0005 |
|---|---|
CVE |
- |
Description |
HTML injection through the GUI |
Date |
28 Jan 2021 |
Severity |
2 - MEDIUM |
CVSSv3 score |
CVSSv3 score not available on NIST NVD. |
Status |
✅ 2.9.2 |
Assessment |
It is possible to manually upload an HTML file that injects in the current view custom HTML wrapped inside style tags. The content inside inside the style tags is injected in the view upon previewing the resulting ingested entity in the platform web GUI. The injected HTML can modify the global variables of the browser, which can temporarily change the currently rendered web GUI view. To revert the style override, affected users can browse back to the previous page in the web GUI. A signed-in user without admin access rights could exploit the vulnerability if they have at least the following permission:
Proof of concept Uploading a crafted HTML file such as the one in the example, and then opening the resulting ingested entity in the platform web GUI changes the style of the text elements to red: <html>
<head></head>
<body>
<style> *{color:red;}</style>
</body>
</html>
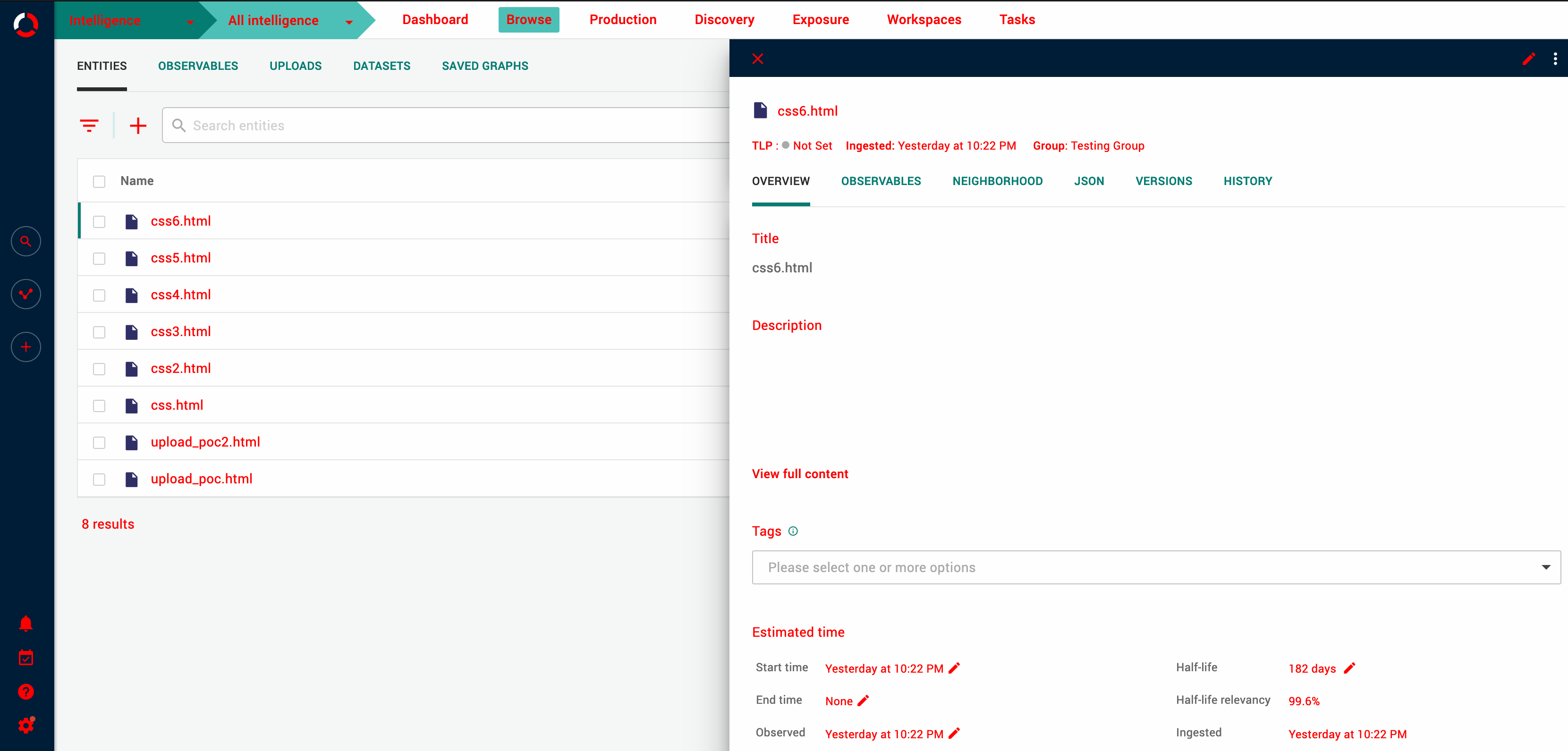
The injected HTML causes the web GUI text to change to red.# |
Mitigation |
To revert the style override, affected users can browse back to the previous page in the web GUI. This vulnerability is addressed in EclecticIQ Platform 2.10.0 by applying stricter HTML sanitization. |
Affected versions |
2.9.1 and earlier. |
Notes |
n.a. |