Work with the app on QRadar#
Caution
This app is no longer supported and this documentation will be removed on 1 December 2024.
Migrate to the new IBM QRadar App for continued support. (Documentation)
Reference tables#
The Threat Intelligence EclecticIQ Platform App for IBM QRadar provides five reference tables:
eiq_data_ip
eiq_data_domain
eiq_data_uri
eiq_data_hash
eiq_data_email
The app ingests content from one or more outgoing feeds set in Install and Configure the app on QRadar and applies them to five different reference tables.
Each table contains Indicator of Compromise (IoC)
values in the eiq_value column in their
respective reference tables.
Use one of these three ways to view data and related metadata that have been ingested into reference tables:
Method |
Description |
|---|---|
Use the IBM QRadar CLI |
For more information on the QRadar CLI, see IBM QRadar: Command reference for reference data utilities. |
Use the IBM QRadar interactive API documentation |
Use the QRadar interactive API documentation to retrieve the contents of a reference table:
|
Use the Reference Data Management App |
Use the IBM App Exchange Reference Data Management App. |
Custom actions#
When you set up the app in Install and Configure the app on QRadar, click Create Custom Actions at the bottom of the EclecticIQ Threat Intelligence Platform Configuration Page to deploy custom actions.
You must click Create Custom Actions each time you change the app configuration to update the custom actions with the new configuration.
The app provides six custom actions on deployment:
Action |
Description |
|---|---|
eiq-sighting_s_ip |
Creates an IPv4 (Source) Sighting on the EclecticIQ Platform. |
eiq_sighting_d_ip (for Destination IP) |
Creates an IPv4 (Destination) Sighting on the EclecticIQ Platform. |
eiq_sighting_hash_md5 |
Creates a MD5 file hash Sighting on the EclecticIQ Platform. |
eiq_sighting_email |
Creates an Email Sighting on the EclecticIQ Platform. |
eiq_sighting_domain |
Creates a Domain Sighting on the EclecticIQ Platform. |
eiq_sighting_uri |
Creates a Sighting on the EclecticIQ Platform. |
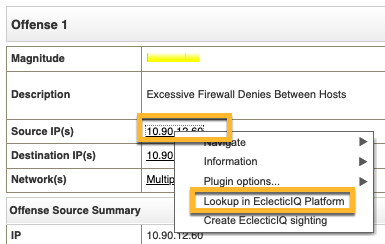
Right click lookup in the QRadar Platform#
To lookup any field in EclecticIQ Platform in QRadar, and get all relevant information on a specific observable:
Right click a field, select More Options.
Click Lookup in EclecticIQ Platform.
A new window will open. If the field has relating data in the EclecticIQ Platform, this data will be displayed along with metadata and all connected entities.
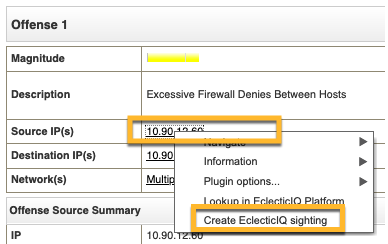
Right click to manually create a new sighting in the QRadar Platform#
You can right-click a field in IBM QRadar to create a new sighting on EclecticIQ Platform using the value of that field:
In IBM QRadar, right click a field and select More Options.
Click Create EclecticIQ Sighting.
Change fields values as required.
Click Create Sighting.
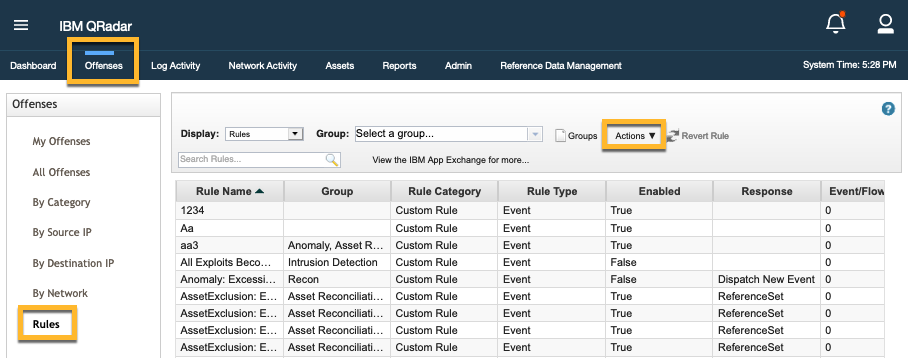
Create an event rule based on ingested data#
You can create rules using ingested threat intelligence data in IBM QRadar.
This set of instructions creates an event rule that is connected to Destination IPs in log events and ingested IP related to threat intelligence:
In IBM QRadar, click the Offenses tab.
Click Rules > Actions > New Event Rule.
In the Rule wizard, select Events and click Next.
Under the Test Group menu, locate:
when Reference Table Key data matches any|all selected event properties and selected reference table column Select operator the value of selected event property
Configure the test rule by clicking on the following parameters and setting these values:
Parameter
Value
Reference Table Key
eiq_data_ip -> eiq_valueSelected event properties
Source IPSelected reference table column
tag_eiqSelect operator
Equalsvalue
Enter an EclecticIQ Platform tag name to find values that match that tag name.
Enter an exact value.
Click Next.
Click Finish.