About taxonomy
To implement a structured tagging scheme, create taxonomies with parent-child relationships.
Tag entities to organize them and make them easier to find.
Structure tags into taxonomies to create a set of controlled categories to classify data and to improve information retrieval in the Intelligence Center.
Taxonomies are structured categories.
Taxonomies make it easier to organize and maintain content, and they help other users find what they are looking for.
They provide a hierarchical framework to structure tags, and to describe parent-child relationships between tagged topics.
Tag relationships provide a reference grid that makes content easier to navigate and to retrieve.
The main benefits of implementing a taxonomy are:
Label information in a structured way to make it easier to navigate and to retrieve.
Provide a reference framework to control entity tagging in the Intelligence Center, so that tags remain meaningful and consistent.
Deliver more accurate search results.
Besides predefined taxonomies, you can create as many custom ones as you need to make it easier for users to discover information in the Intelligence Center data corpus.
Predefined taxonomies
EclecticIQ Intelligence Center ships with the following predefined taxonomy sets:
Admiralty code: based on the two-character Admiralty System code, it helps assess and categorize the reliability of a data source, and the accuracy of the information obtained through a data source.
Kill chain phases: describes the different stages of an attack or an intrusion. By doing so, it helps identify the point(s) in the kill chain where it is possible to intervene with a mitigation action.
The Admiralty code
Use the Admiralty code taxonomy to label entities with tags that define the level of reliability of the data source and the level of accuracy of the entity information.
The Admiralty code taxonomy makes it easier to filter entities and information based on criteria such as relevance and credibility.
It provides intuitive guidance to retrieve reliable and accurate information more easily, while leaving out unwanted data noise.
|
Data source reliability |
Data accuracy |
|
Completely reliable |
Confirmed by other sources |
|
Usually reliable |
Probably True |
|
Fairly reliable |
Possibly True |
|
Not usually reliable |
Doubtful |
|
Reliability cannot be judged |
Improbable |
|
Unreliable |
Truth cannot be judged |
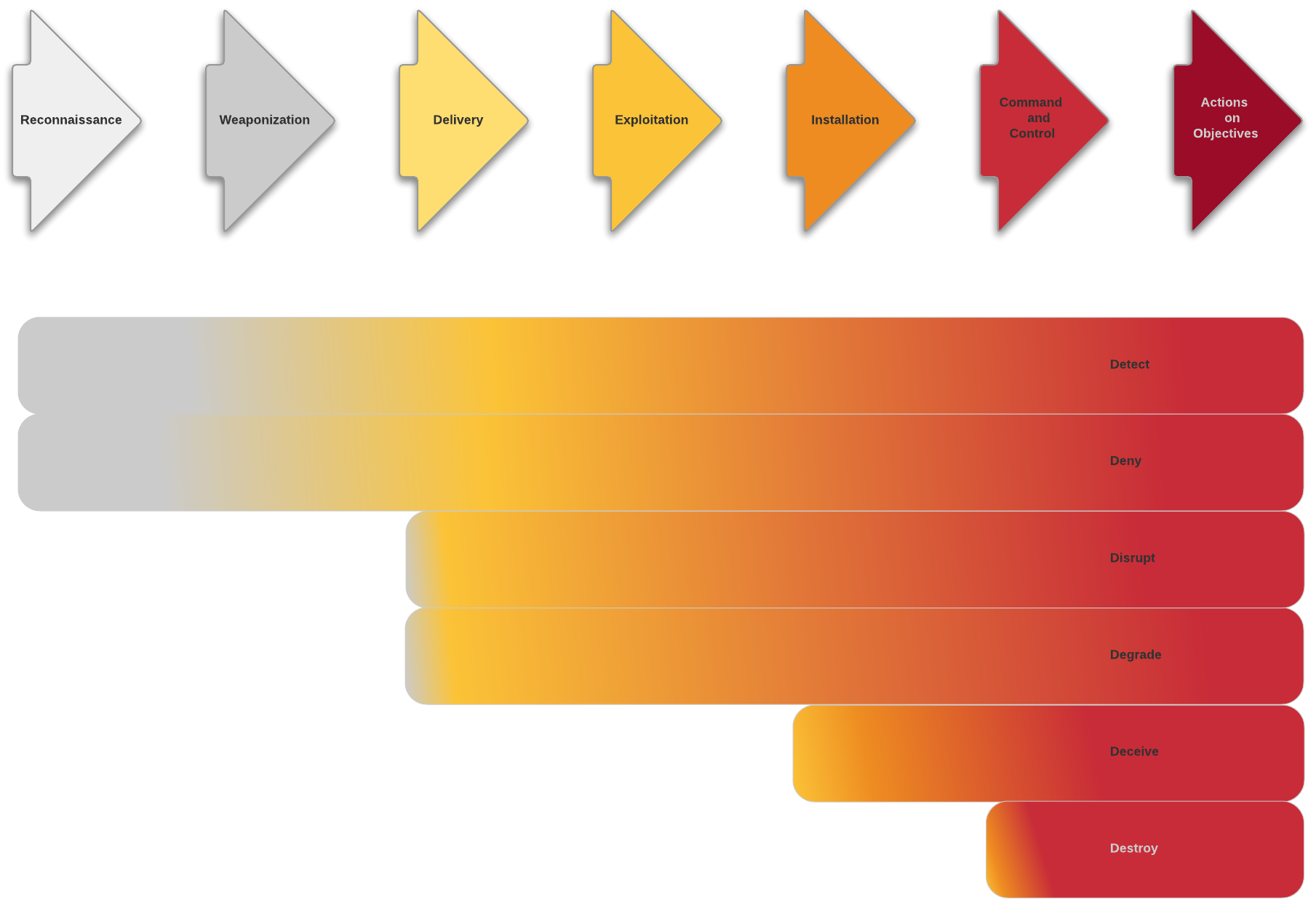
The kill chain
In the context of cyber threat defense, a kill chain aims at encouraging proactive defense, and at implementing adequate courses of action as early as possible in the chain.
The kill chain provides a structured model to:
Break down the actions of an adversary. This helps understand the TTPs the adversary is implementing.
In case of an ongoing attack or intrusion, identify the current stage of the intrusion and quantify damage.
Inspect the kill chain to identify the root cause of the attack or the intrusion.
Plan a defensive course of action to neutralize the adversary.
|
Kill chain phase |
Description |
|
Reconnaissance |
Research, identification and selection of targets, often represented as crawling Internet websites such as conference proceedings and mailing lists for email addresses, social relationships, or information on specific technologies. |
|
Weaponization |
Coupling a remote access trojan with an exploit into a deliverable payload, typically by means of an automated tool (weaponizer). Increasingly, client application data files such as Adobe Portable Document Format (PDF) or Microsoft Office documents serve as the weaponized deliverable. |
|
Delivery |
Transmission of the weapon to the targeted environment. The three most prevalent delivery vectors for weaponized payloads by APT actors, as observed by the Lockheed Martin Computer Incident Response Team (LM-CIRT) for the years 2004-2010, are email attachments, websites, and USB removable media. |
|
Exploitation |
After the weapon is delivered to victim host, exploitation triggers intruders’ code. Most often, exploitation targets an application or operating system vulnerability, but it could also more simply exploit the users themselves or leverage an operating system feature that auto-executes code. |
|
Installation |
Installation of a remote access trojan or backdoor on the victim system allows the adversary to maintain persistence inside the environment. |
|
Command and Control (C2) |
Typically, compromised hosts must beacon outbound to an Internet controller server to establish a C2 channel. APT malware especially requires manual interaction rather than conduct activity automatically. Once the C2 channel establishes, intruders have “hands on the keyboard” access inside the target environment. |
|
Actions on Objectives |
Only now, after progressing through the first six phases, can intruders take actions to achieve their original objectives. Alternatively, the intruders may only desire access to the initial victim box for use as a hop point to compromise additional systems and move laterally inside the network. |
(Source: Intelligence-Driven Computer Network Defense Informed by Analysis of Adversary Campaigns and Intrusion Kill Chains, by Eric M. Hutchins, Michael J. Cloppert, Rohan M. Amin, Ph.D. Paper presented at the 6th Annual International Conference on Information Warfare and Security, Washington, DC, 2011.
|
Course of action |
Description |
|
Detect |
Example: use analytics, auditing, logging tools, and intrusion detection systems (IDS) to detect the intrusion. |
|
Deny |
Example: use patching, firewall rules, access control lists (ACL), and intrusion prevention systems (IPS) to deny exploitation. |
|
Disrupt |
Example: use data execution prevention (DEP) and intrusion prevention systems to block or otherwise disturb exploitation. |
|
Degrade |
Example: use queuing or a tarpit to hinder or otherwise reduce exploitation. |
|
Deceive |
Example: use DNS redirection or a honeypot to divert exploitation to a decoy. |
|
Destroy |
Take control of the attacker’s system to neutralize it. |