Release notes 2.3.1
|
Product |
EclecticIQ Platform |
|
Release version |
2.3.1 |
|
Release date |
2018-11-20 |
|
Summary |
Maintenance release containing bug fixes. |
|
Upgrade impact |
Low |
|
Time to upgrade |
~30 minutes to upgrade
|
|
Time to migrate |
n/a |
EclecticIQ Platform 2.3.1 is a maintenance release. It contains a mix of fixes for important bugs and security issues.
For more details about bugs we fixed, see Important bug fixes below.
For more details about known issues, see Known issues below.
Upgrade
Upgrade path from release 2.0.x(.x) to 2.3.1:
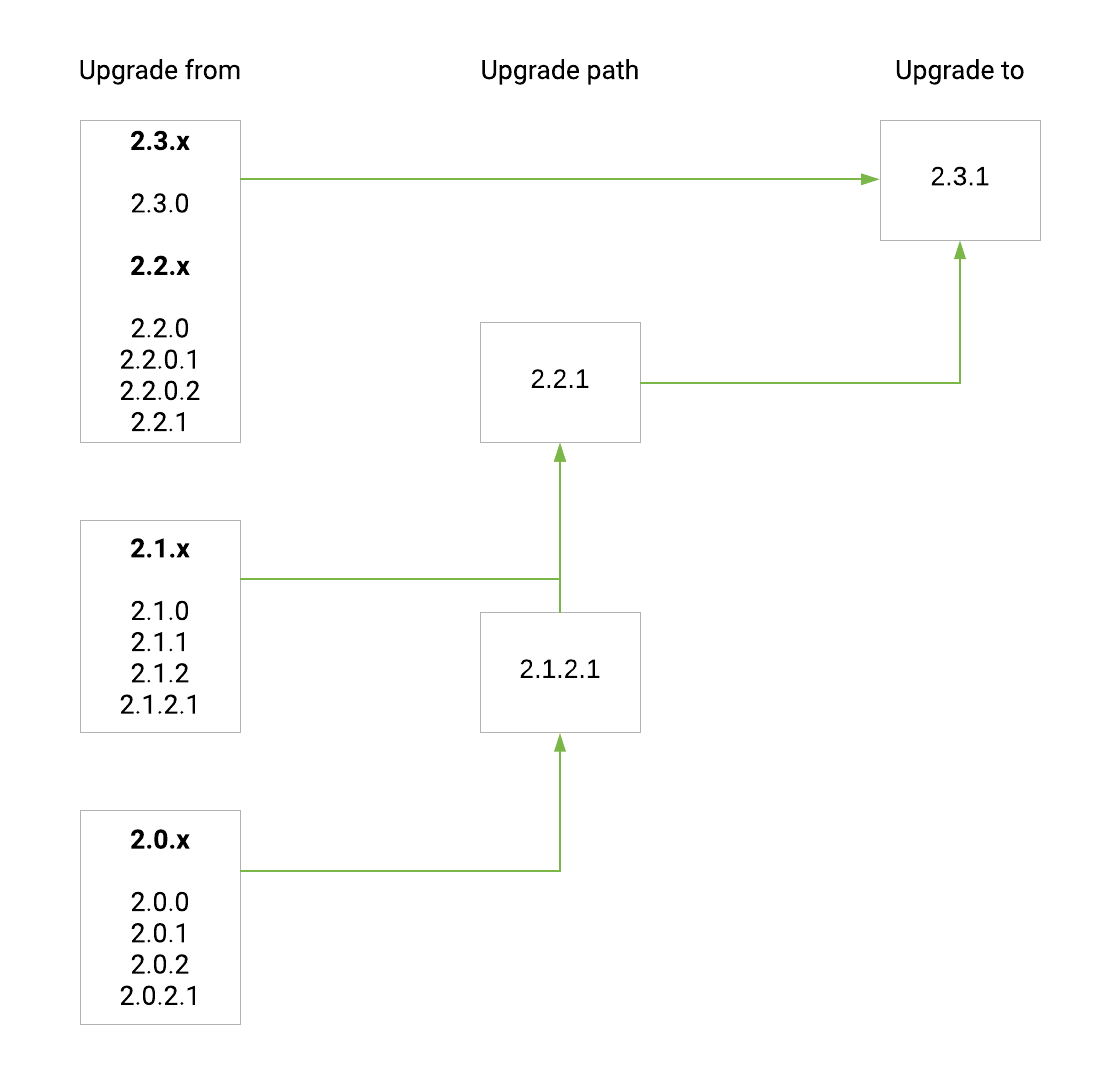
Important bug fixes
This section does not contain all bug fixes; it features a selection of the ones we think are important to mention.
Autocomplete is disabled on the sign-in page.
Entity is successfully deleted without any error messages.
Save and Duplicate works as expected on feed creation.
The sync-data command on Elasticsearch resolves missing entities and it successfully reindexes them in EclecticIQ Platform.
Workspace correlation rule in Discovery rules works as expected.
Last Delivery sorting for Outgoingfeeds works as expected.
Dataset details now links to specific Outgoing feeds.
Feed ingestion works as expected when processing interconnected data.
In a platform-to-platform data exchange setup, a TAXII inbox outgoing feed on the data source platform instance runs correctly, and it correctly transmits the feed data to the TAXII inbox incoming feed on the recipient platform instance.
Tasks of listed workspaces are visible to users with relevant permissions.
The producer identity is displayed when an entity is ingested from a feed or through uploading.
Known issues
Editing/Updating entities creates an external reference for the same entity.
If a user manually adds a sighting to an entity as a characteristic – in the entity editor, under Characteristics, select Characteristic > Sighting – the manually added sighting is not counted in the Exposure view.
If a dataset does not belong to any workspaces, any signed-in platform user can view it.
Current workaround: add it to a workspace.Feed ingestion is slow when processing interconnected data.
Feed ingestion fails intermittently.
We have an automatic retry mechanism in place to reprocess failed packages. In case it does not work as expected, run Retry failed packages from the detail pane.Discovery rule detail pane doesn't show the number of affected entities.
Avatar pictogram is displaced.
Security
The table below includes known security issues, their severity, and mitigation actions.
The state of an issue indicates whether a bug is still open or if it has been fixed in this release.
|
Issue |
Severity |
Present since |
State |
Mitigation |
|
Users need to manually unpin/unlock OS-level dependencies to pull OS-level security patches for dependencies such as OpenJDK. |
Critical |
2.3.0 |
Fixed |
OS-level update repositories are now enabled by default during installation and upgrading operations. |
|
Kibana version is exposed on install. |
Critical |
2.0.0 |
Fixed |
Kibana service was listening on 0.0.0.0. Mitigation: set the binding address to 127.0.0.1. |
|
Unauthorized users are able to upload/edit/download attachments. |
Medium |
2.0.0 |
Fixed |
- |
|
The temporary password (aka OTP: One-Time Password) is logged to the audit trail when a user changes their password. |
High |
2.2.1 |
Fixed |
Replace the temporary password (OTP) with a personal, secure password so that when the OTP is logged, it is not valid anymore. |
|
A user can create rules to access data sources that would normally be disallowed for that user. |
Normal |
2.1.0 |
Open |
Rules are a global construct in the platform and apply to all data. For this reason, ACL does not apply to rule creation. |
|
Information regarding the feed is visible to the user without permissions to view the feed. |
Normal |
2.1.1 |
Open |
ACL restrictions apply to destinations. In this case, this means that any users can view all the destinations an entity was disseminated to. |
|
Poll service configuration is visible to a user without relevant permissions. |
Normal |
2.0.0 |
Open |
When access is granted to read the TAXII configuration, the user is able to see all poll services, even if they do not have the read poll-services permission. Mitigation is to give access to the TAXII configuration to users who are allowed to view all services. |
|
Users can modify Discovery rules without relevant permissions. |
Normal |
2.1.2 |
Open |
Currently permissions do not apply to Discovery rules. |
|
Users can publish a draft entity without relevant permissions. |
Normal |
2.0.0 |
Open |
Entities in Draft status can be modified/published when users have the modify entities permission, and they do not have the modify draft-entities permission. |
Contact
For any questions, and to share your feedback about the documentation, contact us at [email protected] .