Release notes 2.3.0
|
Product |
EclecticIQ Platform |
|
Release version |
2.3.0 |
|
Release date |
2018-09-29 |
|
Summary |
|
|
Upgrade impact |
Medium |
|
Time to upgrade |
~30 minutes to upgrade
|
|
Time to migrate |
|
EclecticIQ Platform 2.3.0 is a minor release. It contains new features as well as bug fixes.
The new features revolve around two themes:
Collaboration with external parties within the Platform
Data management
Release 2.3.0 provides enhanced collaboration within the platform and delegated administrative responsibilities for groups. The enhanced sharing capabilities of workspaces, datasets and graphs ensures that analysts have better control over who can view and collaborate within these features. These features not only improve the cooperation among analysts, but the organization is assured that confidentiality is more easily protected at a granular level.
With release 2.3.0, data retention management allows system administrators to automatically purge threat intelligence in accordance with your organizational policies. The automated deletion of threat intelligence makes it simpler to remove irrelevant information and only retain intelligence that you need.
For more details about new features introduced in this version, see What's new below.
For more details about bugs we fixed, see Important bug fixes below.
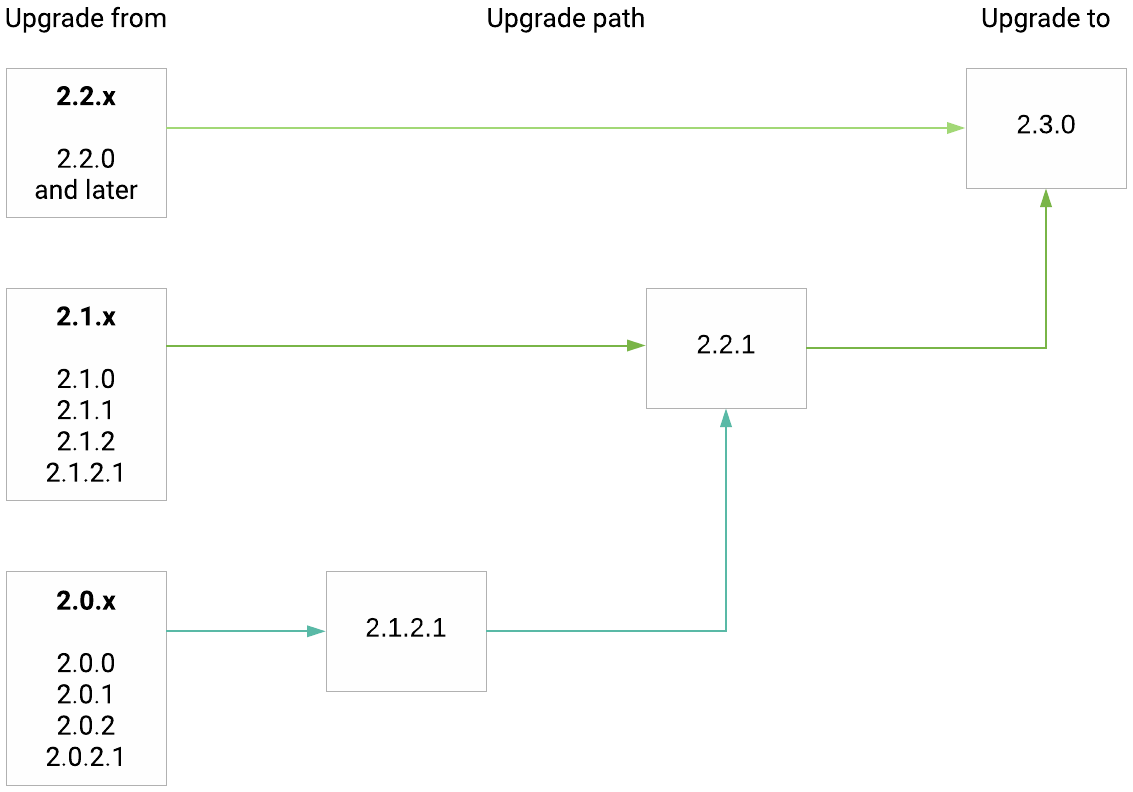
Upgrade
Upgrade path from release 2.0.x(.x) to 2.3.0:
What's new
Delegated group administration
Group administration feature allows EclecticIQ Platform administrators to delegate management of users to their team leaders, making the user administration of the EclecticIQ Platform more scalable and convenient for multiple teams working on the same platform.
Collaboration with external organizations in the platform
This privacy enhancements ensures that only relevant users have the ability to view and collaborate in the associated workspaces, datasets, graphs, and tasks meaning an organization is assured that data confidentiality is protected.
The extended sharing feature provides more granular control over access to better manage sharing the sensitive data.
Policies - Deletion of Entities
System wide policies allows user to delete threat intelligence after a fixed time period automatically. This feature useful from a general data management perspective and also helps in meeting the Global Data Protection Regulation (GDPR) in an efficient way.
Provenance chain enhancements
Both source and Information source provide information about how the threat Intelligence has come into the system. We have improved the following features:
Synchronization of sources allow you to keep your threat intelligence synchronized across multiple EclecticIQ Platform platforms within your own boundaries. With this change, you can keep your sources, secure your intelligence to the correct teams, and keep traceability in the environments.
Information source set up on uploads provides information on creator and creation time of the intelligence. This helps other analysts evaluate the reliability of the source for reports uploaded externally.
Extending STIX 1.2 export to include EclecticIQ metadata
This feature comes in handy if you have built in-house threat intelligence solutions which are based strictly on STIX 1.2. We added metadata in our STIX 1.2 exports using extension mechanisms available in STIX 1.2 and Cybox to allow you to use additional capabilities EclecticIQ Platform and EclecticIQ Fusion Center which go above and beyond STIX 1.2.
This feature requires additional set up, contact our support team for more information.
This is strictly recommended for customers with STIX 1.2-only solutions who decide not to upgrade to this release.
What’s changed
Deprecated dependencies
In previous releases, the platform used StatsD to aggregate metrics. As of this release, we replaced StatsD with Statsite:
Statsite is compatible with StatsD: existing StatsD mappings and indices work with Statsite.
Node.js and statsd-elasticsearch-backend are no longer required.
If you use the platform install script to perform a fresh install or an upgrade from a previous release, the script takes care of the details.
If you manually upgrade the platform, you should remove Node.js and statsd-elasticsearch-backend before you begin the upgrade.
User access control on graphs, datasets, and tasks
Non-private graphs and datasets used to be publicly accessible for viewing to all signed-in platform users.
Now these objects are private by default: upon creation, you need to add them to one or more workspaces. This means that only workspace collaborators can access them.
You can change these settings to allow non-collaborators to view them at a later time.
For further details about user access control for these objects, refer to the following sections:
Important bug fixes
This section does not contain all the bugs, only the ones we think are important to mention.
In Entity rules, filters only display all the sources the current screen.
The Collection name entered when creating an outgoing feed is displayed after saving.
HTML report digest for outgoing feed is fixed.
Known issues
Editing/updating entities creates an external reference for the same entity.
If a user manually adds a sighting to an entity as a characteristic – in the entity editor, under Characteristics, select Characteristic > Sighting – the manually added sighting is not counted in the Exposure view.
If a dataset does not belong to any workspaces, any signed-in platform user can view it.
Current workaround: add it to a workspace.Feed ingestion is slow when processing interconnected data.
Feed ingestion fails intermittently. We have an automatic retry mechanism in place to reprocess failed packages, in case this does not work as expected it is recommended to Retry failed packages from the detail pane.
Security
The table below includes the known security issues, their severity and mitigation actions. The state indicates whether a bug is still open or if it has been fixed in this release.
|
Issue |
Severity |
Present since |
State |
Mitigation |
|
All the launched virtual machines have the same secret key. |
Normal |
2.2.0 |
Fixed |
Secret key for users with 2.2.x platform version are able to change the string manually. For new install, it will generated automatically. |
|
[SAML] Insecure storage location for test SAML configuration file. |
Normal |
2.2.1 |
Fixed |
By default the SAML configuration helper using this configuration file is not enabled. So if you do not use this functionality introduced in 2.2.1, there is no impact. |
|
Modify saved-searches is removed for the users. |
Small |
2.1.2 |
Fixed |
None. This permission was present in the UI with no advantage and is now removed. |
|
A user can create rules to access data sources that would normally be disallowed for that user. |
Normal |
2.1.0 |
Open |
Rules are a global construct in the platform and apply to all data. For this reason, ACL's are not applied to the rule creation. Mitigation is to only allow people with full access to create rules inside the platform. |
|
Information regarding the feed is visible to the user without permissions to view the feed. |
Normal |
2.1.1 |
Open |
Destinations is under ACL restrictions, which this allows any user to view all the destinations to which an entity was disseminated. Mitigation is to avoid using descriptive names for feeds and hide the actual destination. |
|
Poll service configuration is visible to a user without relevant permissions. |
Normal |
2.0.0 |
Open |
When access is granted to read TAXII Configuration, the user is able to see all Poll services even if they do not have Read poll services. Mitigation is to give access to TAXII Configuration to users who are allowed to view all services. . |
|
Users can modify Discovery rules without relevant permissions. |
Normal |
2.1.2 |
Open |
Discovery rules do not use permissions as of now. This will be addressed during permission refactoring. |
|
Users can publish a draft entity without relevant permissions. |
Normal |
2.0.0 |
Open |
Entities with Draft status can be modified/published even if the user does not have modify draft-entities permission. It is possible due to modify entities permission. To make sure permissions are aligned, always use both permissions or neither. |
Contact
For any questions, and to share your feedback about the documentation, contact us at [email protected] .