Working with the EclecticIQ Platform App for Splunk
This application is no longer supported.
From 22 August 2022, use both of the following apps instead:
Overview
The Threat Intelligence EclecticIQ Platform App provides seven default dashboards for you to monitor:
Observables received from EclecticIQ Platform
Matches detected
Alerts triggered
To get the dashboards to display data, you must have:
Configured the Threat Intelligence EclecticIQ Platform App to connect to your EclecticIQ Platform instance.
Enabled Working with the EclecticIQ Platform App for Splunk#Alerts.
List of dashboards
These dashboards can be accessed from the top navigation bar.
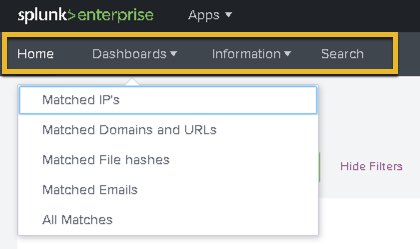
Dashboards available by default:
|
Tab |
Dashboard and description |
|
Home |
Home: Provides an overview of
|
|
Dashboards |
|
|
Information |
|
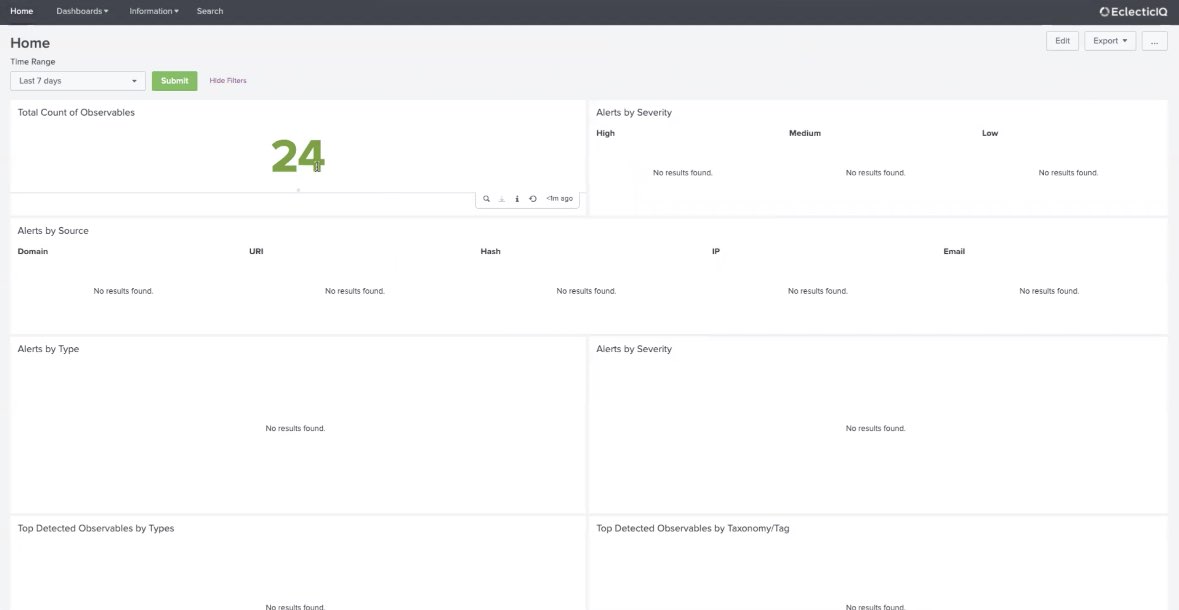
You can customize each dashboard by clicking Edit in the top-right corner.
Example of Threat Intelligence EclecticIQ Platform App Home dashboard:
Make any dashboard the Splunk Web Home dashboard
Open the dashboard you want ot set as your Home dashboard.
Go to the top-right corner of the view and click
.
Select Set as Home dashboard.
View application logs
In the event that you need to troubleshoot the app, view the application log:
Open the Threat Intelligence EclecticIQ Platform App in Splunk Web.
In the top navigation bar, click Information > Application Logs.
To manage what log levels are displayed, go to the App settings (Information > Edit app settings), and edit the Scripts Log Level field.
Scripts
The Threat Intelligence EclecticIQ Platform App ships with two scripts:
Collection script
The script that collects outgoing feed data from EclecticIQ Platform is: eiq_collect_feeds.py.
Inputs stanza: [script://$SPLUNK_HOME/etc/apps/SA-EclecticIQ/bin/eiq_collect_feeds.py].
By default, the collection script is configured to run every 20
minutes (cron schedule: */20 * * * *).
Sightings script
The script that sends sightings to EclecticIQ Platform is: eiq_send_sightings.py.
Inputs stanza: [script://$SPLUNK_HOME/etc/apps/SA-EclecticIQ/bin/eiq_send_sightings.py].
By default, the collection script is configured to run every 15 minutes (cron schedule: */15 * * * *).
Manage scripts
This section describes how to manage scripts provided with the app.
Enable/disable a script:
In the top navigation bar, click Settings > Data inputs.
Under Local inputs, click Scripts.
In the row of the script you want to enable/disable, go to the Status column.
Click Enable or Disable.
Edit the interval cron expression of a script:
In the top navigation bar, click Settings > Data inputs.
Select Scripts.
Click the script you want to edit.
In the Interval field, change the interval.
Click Save.
For further details on Splunk cron expressions, see the official Splunk documentation on cron expressions and their answers to common questions on cron expressions.
KV store
The EclecticIQ Platform app creates three KV stores in Splunk:
eiq_ioc_list (Downloaded observables)
eiq_feed_list (Meta Information about Outgoing Feeds)
eiq_alerts (Alerts results)
Do not manually edit the KV stores.
The collection script writes the downloaded threat intelligence directly to these KV stores, and is search head cluster -aware.
Alerts
The Threat Intelligence EclecticIQ Platform App comes packaged with two different saved searches. Both are disabled by default, and must be enabled before alerts can be triggered by the app.
List of alerts
EclecticIQ alert
The EclecticIQ alert saved search is a plain-text saved search that triggers an alert when it finds matches for observables collected from the connected EclecticIQ Platform instance.
Enabling both EclecticIQ alert and any one of the EclecticIQ tstats Threat Intelligence alerts may produce duplicate results.
(Recommended) EclecticIQ tstats Threat Intelligence alert
Requires the Splunk Common Information Model (CIM).
We recommend using these alerts over the EclecticIQ alert saved search.
The EclecticIQ tstats Threat Intelligence alert is a group of five saved searches that use Splunk data model acceleration.
From Threat Intelligence EclecticIQ Platform App version 2.5.4 onwards, the EclecticIQ tstats Threat Intelligence alert is split into five different alerts:
EclecticIQ tstats Threat Intelligence alert - Domain
EclecticIQ tstats Threat Intelligence alert - Email
EclecticIQ tstats Threat Intelligence alert - Hash
EclecticIQ tstats Threat Intelligence alert - Source/Destination
EclecticIQ tstats Threat Intelligence alert - URL
Each alert is triggered when the saved search runs and finds events that match its respective observable types.
For example, the EclecticIQ tstats Threat Intelligence alert - Domain saved search triggers an alert when it finds an event that matches a domain observable collected from the connected EclecticIQ Platform instance.
Enable alerts
To enable the saved searches:
Open Splunk Web.
In the top navigation bar, click Settings > All configurations.
In the All configurations page, set the filter to only display entries for EclecticIQ Platform App (SA-EclecticIQ).
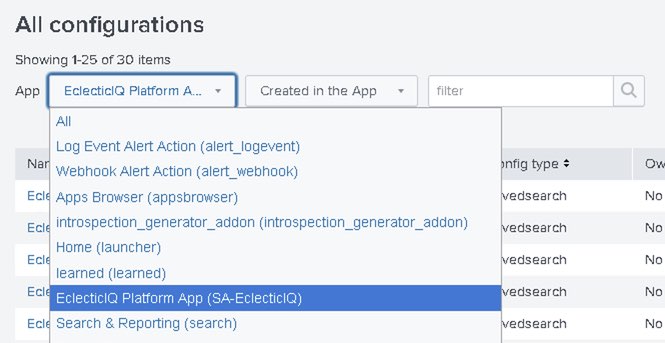
Do this by selecting from the drop-down menus next to App:
EclecticIQ Platform App (SA-EclecticIQ)
Created in the App
Click Enable in the Status column for these saved searches:
EclecticIQ alert
EclecticIQ tstats Threat Intelligence alert - Domain
EclecticIQ tstats Threat Intelligence alert - Email
EclecticIQ tstats Threat Intelligence alert - Hash
EclecticIQ tstats Threat Intelligence alert - Source/Destination
EclecticIQ tstats Threat Intelligence alert - URL
Manage how frequently alerts are run
You can manage how frequently the saved search for an alert is run by editing the CRON interval for that alert.
To edit the CRON interval of an alert
In the top navigation bar, click Settings > All configurations.
Locate the alert you want to configure, and click on its name.
Edit the contents of the Cron Expression field. Change it to the desired time and date the saved search should run.
Uninstall
To uninstall the Threat Intelligence EclecticIQ Platform App, open the terminal on your Splunk host and run:
$SPLUNK_HOME/bin/splunk remove app SA-EclecticIQOr remove the app directory manually by running:
Removing data with rm -rf is irreversible.
rm -rf SPLUNK_HOME/etc/apps/SA-EclecticIQAfter the command completes, restart Splunk:
$SPLUNK_HOME/bin/splunk restart