Release notes 2.4.0
|
Product |
EclecticIQ Platform |
|
Release version |
2.4.0 |
|
Release date |
22 May 2019 |
|
Summary |
Minor release |
|
Upgrade impact |
Medium |
|
Time to upgrade |
~30 minutes to upgrade
|
|
Time to migrate |
|
EclecticIQ Platform 2.4.0 is a minor release. It contains new features as well as bug fixes.
The new features are mainly usability improvements aimed at enhancing the overall user experience of EclecticIQ Platform.
This results in less repetition/scrolling/clicks/clutter, and more relevant information.
All these changes together make working with EclecticIQ Platform on a daily basis easier, faster, and more efficient.
For more information about new features and functionality, see What's new below.
For more information about enhancements and improvements, see What's changed below.
For more information about bugs we fixed, see Important bug fixes below.
For more information about security issues we addressed, see Security issues and mitigation actions below.
Upgrade
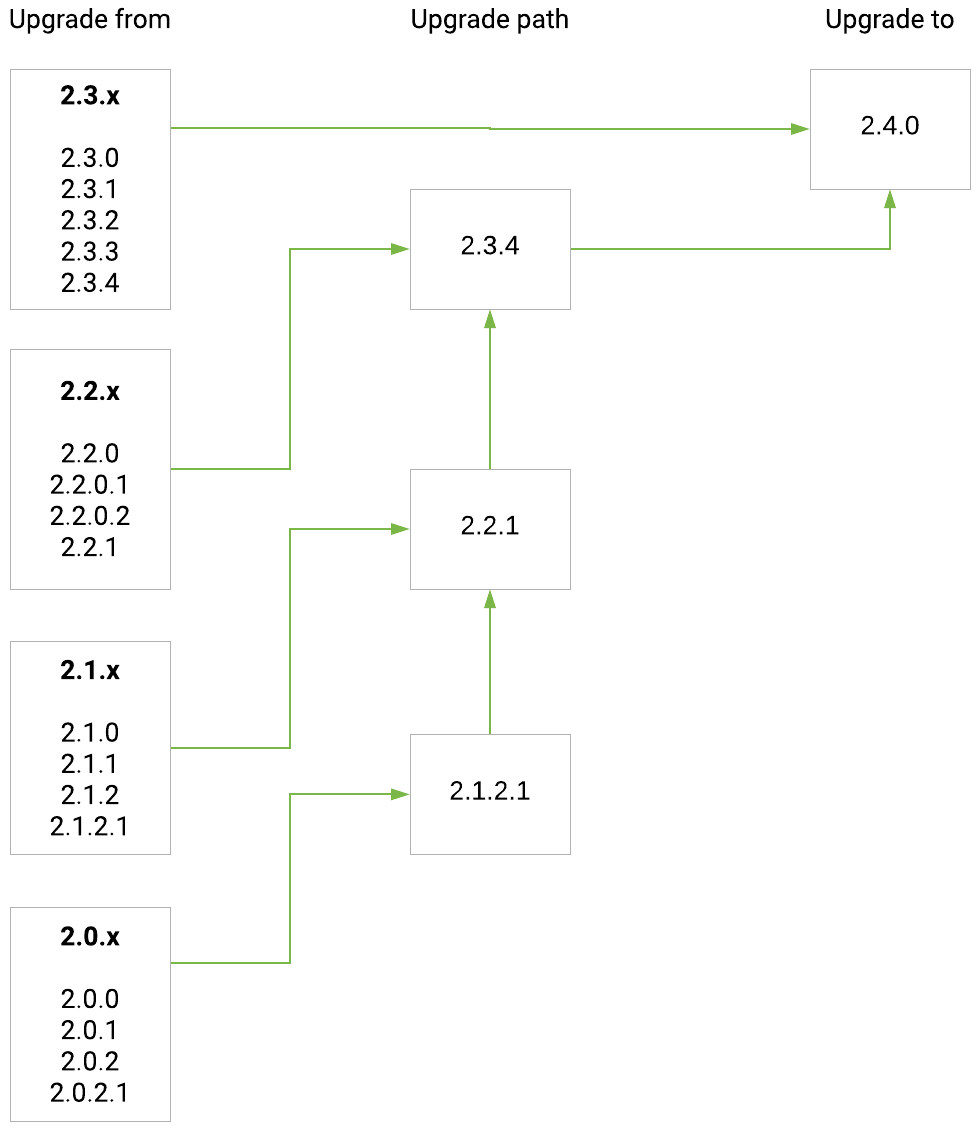
Upgrade path from release 2.0.x(.x) to 2.4.0:
What's new
Bulk tagging
Bulk tagging enables you to manage tags for multiple entities at once, directly from List or Graph views, rather than one entity at a time.
This helps you to avoid tagging mistakes that typically result from performing repetitive actions.SAML single logoff
If your identity provider uses SAML to authenticate and authorize users for multiple service providers, the support for single logoff ensures that your analysts are logged out of EclecticIQ Platform, no matter which service triggers the logoff action.
This means you do not have to worry about left-open sessions that might make services vulnerable to attacks.Entity detail pane header
The newly designed header of the detail pane provides a more consistent and common way of interacting with panes.
It provides you with a fixed header and an action menu that is always visible, even when scrolling down.
This makes working with the pane faster and more intuitive.
What's changed
UI improvements
We updated the UI for Group admin and User groups and adjusted the documentation.
The new layout matches the one used for setting feed filters, which makes the platform more cohesive.Statsite replaced StasD
For metrics aggregation, we replaced StasD with Statsite. Statsite is compatible with StasD, and uses the same protocol.Detecting and refanging defanged URIs during ingestion
We improved the refanging logic to detect and refang defanged URIs during ingestion to be more effective and accurate.
More defanged URIs are now detected and refanged.Ingestion performance
We made various improvements to increase the ingestion performance of several known problematic scenarios.External reference handling
It is now possible to filter out external references, such as search, browse, discovery, and exposure, in entity tables.
This gives you a clutter-free view, while still being able to see if external references exist.
It also makes it easier to see the bigger picture, and if there is more intelligence available for the entity you are interested in.Improved search tokenization
We have improved our search tokenization, and the new means to tokenize allows you to be more specific in matching observables when creating searches, dynamic datasets, or rules.
This increases the means of matching for data, giving higher confidence in that you find all relevant information.
New fields are available side-by-side with existing ones, so that the changes to the tokenization mechanism do not break existing queries.Tagging rules
There were some inconsistencies in tagging rules execution. This has now been fixed.Allowing package operations
Users without access to a particular incoming feed were able to reprocess/purge packages from that feed.
This should not have been possible, and has now been fixed.
Users now have to properly check source access before allowing package operations.Source access on observables
In the Observables view, sources are now properly filtered according to the user's Allowed sources settings.Audit logging
The platform's audit logging to prevent credential exposure did not work correctly. This has now been fixed.Updated permissions
We updated our permissions. Some have been added, some have been removed, and some have been changed.
Below is a list of the affected permissions.New permissions:
modify discovery-rules (to align permissions across all types of rules)
modify enrichers (enables more granular access to the platform functionalities )
modify taxii-services (replaces the 4 removed modify permissions concerning -services)
read discovery-rules ( to align permissions across all types of rules)
read taxii-services (replaces the 5 removed read permissions concerning -services)
read traceback-logs (descriptive errors that contain sensitive information can now be hidden from users without this permission)
reset password (enables more granular user management actions control)
lock/unlock users (enables more granular user management actions control)
Removed permissions:
modify enrichment rule-criterions (this permission was too specific and already covered by other higher-level permissions)
modify collection-management-services (replaced by modify taxii-services)
modify discovery-services (replaced by modify taxii-services)
modify inbox-services (replaced by modify taxii-services)
modify poll-services (replaced by modify taxii-services)
modify notifications (this permission was not used or needed)
modify task-counters (this permission was too specific and already covered by other higher-level permissions)
read enrichment rule-criterions (this permission was too specific and already covered by other higher-level permissions)
read collection-management-services (replaced by read taxii-services)
read discovery-services (replaced by read taxii-services)
read inbox-services (replaced by read taxii-services)
read poll-services (replaced by read taxii-services)
read services (replaced by read taxii-services)
read task-counters (this permission was too specific and already covered by other higher-level permissions)
Updates permissions:
read history-events
read tasks
read enrichers
read entity-drafts
modify entity-drafts
read audit-trail
From now on, a permission to modify implies a permission to read.
Users with a modify access permission for a resource do not need a separate read permission.
Customers that use self-created user-groups/roles may need to review the permission sets involved.
Important bug fixes
This section is not an exhaustive list of all the important bug fixes we shipped with this release.
Timestamps
EclecticIQ Platform now displays the timestamp from the successful and failed downloads.
This means that even if the last run has failed, extensions that return timestamp in ctx.submit will resume correctly, even if their last poll failed.Updating statsite
We discovered that updating Statsite would cause the statsite service to stop running.
This has been fixed by enabling and starting the statsite service manually, after the upgrade.Running Outgoing feeds
After creating and running an Outgoing feed with some observables, the widgets Exported observables by type and Exported observables by feed did not show any information.
We discovered that the problem occurred when the statsite service was down.
Once the statsite service was back on, the mentioned widgets were once again working as expected.Purging large incoming feeds
It was not possible to purge incoming feeds with more than 1 million ingested entities through the GUI.
The task would start running, but the feed would not be correctly deleted, yet the relevant UI options would become unavailable in the GUI.
The workaround required running a command in a Python shell. However, non-admin users often have no shell access.
We fixed the problem, and it is now again possible to purge large incoming feeds.Incorrect extra error message for invalid Override value
When editing an entity, selecting the Override value option and entering an invalid value for half-life (such as -1), did not only display an error message below this option, but also an incorrectly displayed an error message below the Use default value option next to it.
This has now been fixed. When you now enter an invalid Override value, only the correct error message is displayed.Task widget not working
The Task change widget was not working properly due to wrong third-party library import. This has now been fixed.
Execution schedule value
In the Create outgoing feed view, under the Schedule section, it was not possible to select a value for Execution schedule.
The drop-down menu closed as soon as it was opened. This has now been fixed.
UI/JS-errors
Several minor UI- and JS-errors have been fixed.Browse view did not display latest entities
When sorting entities by ingestion date (Timestamp) in the Browse view, the most recently ingested entities would not be included, although it would be possible to retrieve them by running a targeted search.
We have given searches have more time to complete execution. If they fail to complete because of a timeout, a message is displayed to notify users.
Security issues and mitigation actions
The following table lists known security issues, their severity, and the corresponding mitigation actions.
The state of an issue indicates whether a bug is still open, or if it was fixed in this release.
For more information, see All security issues and mitigation actions for a complete and up-to-date overview of open and fixed security issues.
|
ID |
CVE |
Description |
Severity |
Status |
Affected versions |
|
- |
marked is vulnerable to regular expression denial of service |
2 - MEDIUM |
|
2.3.4 and 2.4.0 |
|
|
- |
Cross-site scripting (XSS) vulnerability in webpack bundle analyzer |
2 - MEDIUM |
|
2.4.0 and earlier. |
|
|
SSL connection with improper authentication in urllib3 versions 1.24.1 and earlier |
3 - HIGH |
|
2.3.4 and earlier. |
||
|
CRLF injection and HTTP header manipulation in urllib3 |
2 - MEDIUM |
|
2.3.4 and earlier |
||
|
- |
js-yaml 3.13.0 and earlier are vulnerable to code injection |
3 - HIGH |
|
None |
|
|
SQL injection through order_by in SQLAlchemy 1.2.17 and 1.3.x to 1.3.0b2 |
4 - CRITICAL |
|
None |
||
|
SQL injection through group_by in SQLAlchemy 1.2.17 |
3 - HIGH |
|
None |
||
|
Jinja2 2.10 and earlier allows sandbox escape |
3 - HIGH |
|
None |
||
|
lodash enables prototype pollution |
2 - MEDIUM |
|
2.3.4 and earlier. |
||
|
lodash enables prototype pollution |
4 - CRITICAL |
|
2.1.0 to 2.3.4 included. |
||
|
- |
Stack trace information is available to non admin users |
1 - LOW |
|
2.3.1 to 2.3.4 included. |
Contact
For any questions, and to share your feedback about the documentation, contact us at [email protected] .