Release notes 2.3.2
|
Product |
EclecticIQ Platform |
|
Release version |
2.3.2 |
|
Release date |
2019-01-08 |
|
Summary |
Maintenance release containing bug fixes |
|
Upgrade impact |
Low |
|
Time to upgrade |
~30 minutes to upgrade
|
|
Time to migrate |
n/a |
EclecticIQ Platform 2.3.2 is a maintenance release. It contains a mix of fixes for bugs and security issues.
For more details about bugs we fixed, see Important bug fixes below.
For more details about security issues we addressed, see Security issues and mitigation actions below.
For more details about known issues, see Known issues below.
Upgrade
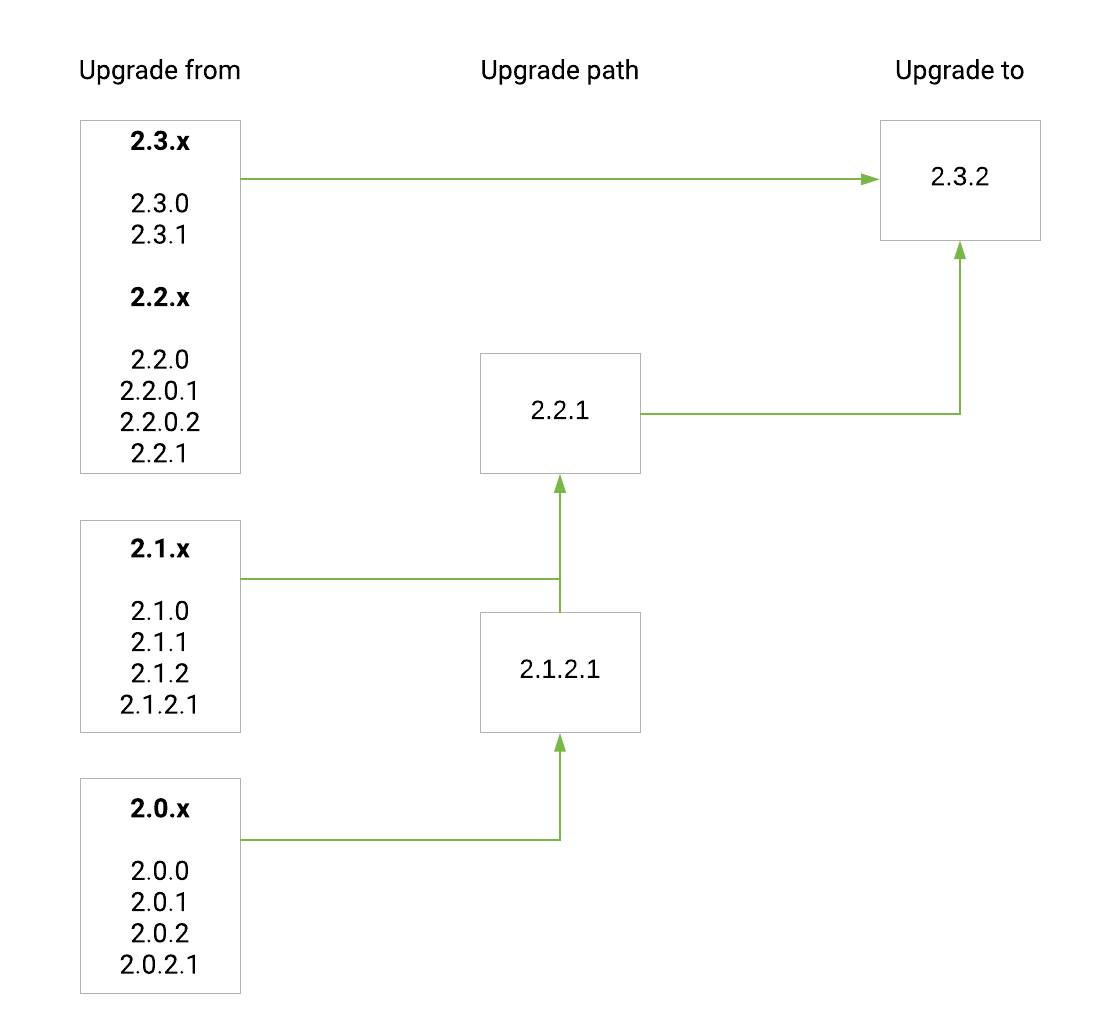
Upgrade path from release 2.0.x(.x) to 2.3.2:
Important bug fixes
This section is not an exhaustive list of all the important bug fixes we shipped with this release.
Reassigning an existing task to the currently assigned user by selecting Actions > Reassign on the task detail panel would cause the Reassign task pop-up dialog to hang, and it would not be possible to complete the action.
Now the process works as expected, and it is possible to reassign user tasks to any registered platform users, included the currently assigned one, provided they have the appropriate access rights to the tasks in questions and to the corresponding workspaces.Changing the status of an existing task by selecting Complete, Reopen, Cancel, or Delete from the
context menu would return an incorrect pop-up notification message.
Now the pop-up notification message communicates the correct task status change, after it is applied.A signed-in user with non-administrative rights and without appropriate modify permissions could still access GUI options to modify saved assets and resources.
For example, a user without the permission to modify taxonomy entries could access the> Edit and
> Delete options on the Data configuration > Taxonomies overview.
Although such users could click modify actions, the selected command would fail to execute because of insufficient permissions.
Now if users do not have the appropriate permissions to initiate and execute an action, they do not have access to it.Changing the name of an existing entity using the inline edit option and the Edit entity alias pop-up dialog would not reflect the entity name change on the entity overview list.
Now when you change an entity name on the fly using the the inline editor, the new name is correctly displayed also on the entity overview list.Entities on the Intelligence > All intelligence > Browse overview would take longer to load, compared to other similar views such as Production or Discovery.
Now entity loading on the Intelligence > All intelligence > Browse overview is faster and closer to other similar views.Draft entities would not always be attributed to the correct author, when created sequentially with different signed-in user profiles.
Now draft entities always store the correct author details.After manually uploading a batch of files, it would not be possible to manually reprocess the most recently uploaded one by selecting
> Reprocess on the Intelligence > All intelligence > Browse > Uploads view.
Now it is possible to successfully reprocess manually uploaded files.While creating an entity rule, users can click Preview rule to test the rule, and to review the matching results it returns.
Preview rule would not work when using TLP as a selection criterion; the action returned an error message, instead.
Now Preview rule works as expected, also when using TLP as a selection criterion for the entity rule.A data retention policy rule designed to delete matching entities would run, but it would not delete matching entities as expected.
Now data retention policy rules targeting specific entities for deletion run and work as expected.Filtering observables by
> Relation on the Observables tab of an entity detail pane would return a JavaScript error in the web browser console, and the applied filter would not work.
Now it is possible to successfully filter entity observables by> Relation on the Observables tab of an entity detail pane.
If a user entered an integer in the free-text filter input field on the Data configuration > Policies overview to filter policy results, the filter would return a JavaScript error.
Now an integer in the free-text filter input field on the Data configuration > Policies overview is interpreted as a literal, and the filter returns matching policies containing the specified integer in the policy name.As of release 2.3.0 Statsite replaces StatsD. This change broke some platform dashboard widgets, which would not display any data any longer.
For example: Exported entities by feed and Exported entities by type.
Now Statsite data is correctly indexed in Elasticsearch, and dashboard widgets display data as expected.
Security issues and mitigation actions
The following table lists known security issues, their severity, and the corresponding mitigation actions.
The state of an issue indicates whether a bug is still open, or if it was fixed in this release.
For more information, see All security issues and mitigation actions for a complete and up-to-date overview of open and fixed security issues.
|
Issue |
Severity |
Since |
State |
Mitigation |
|
Users could send GET and PUT requests to the /private/workspaces/{workspace_ID} API endpoint to obtain data from and to overwrite data in existing workspaces, even without having any access rights to the target workspaces. |
3 - HIGH |
- |
|
n/a |
|
Users could send POST requests to the /private/workspace-comments/{comment_ID} API endpoint to modify existing workspace comments, even without having any access rights to the target workspaces. |
3 - HIGH |
2.3.0 |
|
n/a |
|
Users could send POST requests to the /private/blobs/{package_ID}/reprocess or to the /private/blobs/{package_ID}/purge API endpoints to reprocess or to purge specific packages ingested through an incoming feed, even without having any access rights to the incoming feed data source(s). |
3 - HIGH |
2.3.0 |
|
n/a |
|
urllib3 HTTP client versions earlier than 1.23 do not remove the Authorization HTTP header when following a cross-origin redirect – a redirect with a different host, port, or scheme. This can allow for credentials in the Authorization header to become exposed to unintended hosts or be transmitted in clear text. See also: CVE-2018-20060 |
1 - LOW |
2.2.0 |
|
n/a |
|
During a user-triggered password reset, the temporary password / one-time-password (OTP) is stored in the audit trail, which is accessible to platform API users. This creates a window of time where a malicious user could reset the password of another user. Now this data is removed from the audit trail. |
1 - LOW |
2.3.0 |
|
n/a |
|
Registered platform users with an inactive status could reset their password, and they would receive an email notification with further instructions and a reset link. |
1 - LOW |
2.2.0 |
|
n/a |
|
A user with the modify groups permission and without the read sources permission can view data sources they do not have access to. They can also assign data sources to themselves or to other users. They can achieve these goals through API calls. This allows users to access and to apply actions on platform data that would normally not be accessible to them. |
3 - HIGH |
2.3.2 |
|
Permissions will be updated to allow users to access only the allowed data sources of the groups they are members of. |
|
A user can run rules and search queries to access data sources that would normally not be visible to them because they require a different set of permissions than the ones granted to the user. This allows users to apply actions that may accidentally modify the affected assets in an unexpected or undesirable way. |
2 - MEDIUM |
2.1.0 |
|
Permissions will be updated to allow users to access only the allowed data sources of the groups they are members of. |
|
Users without the modify rules permission can edit and delete rules through the corresponding context-menu options. They can also edit and delete rules by selecting Actions > Edit and Actions > Delete on a rule detail pane. |
2 - MEDIUM |
2.1.2 |
|
To prevent users from editing and deleting rules, make sure they lack the modify rules permission. |
|
Users with the modify poll-services permission and without the read poll-services permission can access the TAXII poll configuration through the GUI by selecting > STIX and TAXII > TAXII. |
2 - MEDIUM |
2.0.0 |
|
To prevent users from accessing the TAXII poll configuration, make sure they lack both the modify poll-services and the read poll-services permissions. |
|
Some manual input fields in the GUI – for example, the Details input field on a workspace dashboard – parse HTML instead of rendering it as raw source. For example, a base64 encoded image is rendered as an image instead of raw HTML markup. Users could use such an input field to inject insecure code, which would be parsed. |
2 - MEDIUM |
2.3.0 |
|
|
|
An incoming feed using the HTTP download transport type can access internal components. For example, a user could set the transport configuration URL to http://localhost:9001/index.html?processname=platform-api&action=stop to reach the platform-api component and stop it upon running the incoming feed task. |
2 - MEDIUM |
2.3.0 |
|
Possible workarounds to mitigate the issue:
Long-term mitigation:
|
|
Kibana versions earlier than 6.4.3 and 5.6.13 contain an arbitrary file inclusion flaw in the Console plugin. An attacker with access to the Kibana Console API can send a request that will attempt to execute JavaScript code. This could possibly lead to an attacker executing arbitrary commands with Kibana process permissions on the host system. The bug prints the return only to the Kibana logs, which makes it relatively hard to exploit. If a user could upload a JavaScript file to the server, it would increase the impact up to the level indicated by the CVSS base score. However, the platform stores most files in the PostgreSQL database, and temporary files are separated from the Kibana user with permissions. As a result, we have not found an execution path on platform installations that follow our build advice. See also: CVE-2018-17246 |
2 - MEDIUM |
2.0.0 |
|
Upgrade the ELK stack to 5.6.14. |
|
When a platform action or operation fails to correctly execute, a stack trace may be available to help sysadmins troubleshoot the problem. Currently, the stack trace is accessible to admin and to non-admin users. |
1 - LOW |
2.3.1 |
|
The field with the stack trace information should be available only to admin users; it should be empty for non-admin users. |
|
A user with the modify entities permission and without the modify draft-entities permission can promote an entity from draft to publication. Currently modify entities acts like a superset of modify draft-entities. modify entities should affect only entities in the published state, and it should not impact entities in draft state. |
1 - LOW |
2.1.2 |
|
To prevent users from publishing draft entities, make sure they lack both the modify entities and the modify draft-entities permissions. |
|
When navigating the application, and possibly when navigating to an external URL, the Nginx server includes the Referer header. This could provide a potential attacker with the external IP address, or the internal system name of the application, thus creating a view of the potential attack surface. |
1 - LOW |
2.3.1 |
|
Set the Referrer-Policy header value in Nginx to no-referrer. Example: add_header 'Referrer-Policy' 'no-referrer';See also: |
Known issues
Users lacking an appropriate TLP access level can click an ingested entity, open the detail pane of the selected entity, and then access the Actions > Download original menu option.
For example, a user with a TLP White access level can click the access the Actions > Download original menu option of an entity with TLP Green.
However, since the user does not have the necessary access level, clicking the menu option does not trigger the corresponding entity download action.While working on a report, analysts may want to save it, then go back to it for further editing, and then save it again, until the report is ready, and they can publish it.
Occasionally, upon opening a saved report to edit it, some or all the content in the Analysis section of the report is missing. The other sections in the report retain their content, as expected.
This behavior is infrequent and unpredictable.Sometimes it is not possible to successfully delete or purge the content of a large incoming feed (> 1 million entities with correlations). The platform GUI grays out the feed. As a consequence, it is not possible to attempt deleting or purging it again from the GUI.
Workaround:Open a terminal session, and sign in to the platform.
Log in as the eclecticiq user:
sudo-u eclecticiq
This also starts the Python virtual environment for the platform.Run the following command(s) to manually purge an incoming feed:
eiq-platform purge-incoming-feed --incoming-feed-id=${incoming_feed_id}
--incoming-feed-id is a mandatory argument.
Its value is an integer corresponding to the ID of the incoming feed you want to purge.
Loading more than 100 objects – entities, observables, and relationships – on the graph may negatively impact GUI performance because the loaded data is heavy on memory resources.
Enriching entities with the Fox-IT InTELL Portal enricher returns a successful notification on the GUI, but it records an error in the /var/log/eclecticiq/task-worker-enrichers-priority.log file.
The enrichment operation fails.When exchanging data between two platform instances using STIX as a content type for the source data on the publishing platform instance, ingestion into the recipient platform instance produces a new entity for each version of an ingested entity instead of resulting in an entity that is updated with as many versions as the corresponding source entity in the publishing platform instance.
This occurs especially when STIX entities ingested in the recipient platform instance lack a STIX ID in the publishing platform instance.If package ingestion fails for a package, even after automatically attempting to ingest it again, the GUI may display a successful ingestion status for that package, although no entities were ingested.
Contact
For any questions, and to share your feedback about the documentation, contact us at [email protected] .