MITRE ATTACK
Add MITRE ATT&CK classifications to entities to provide additional context for your intelligence.
Contents
MITRE ATT&CK on the Intelligence Center
The Intelligence Center provides MITRE ATT&CK classifications that you can apply to entities. These ATT&CK classifications are based on ATT&CK v8.2.
Currently, only Enterprise ATT&CK classifications are available.
Permissions
To be able to assign ATT&CK classifications to an entity, your user must have a role with these permissions:
read attack
modify entities
All users can still search for and see ATT&CK classifications assigned to entities without the read attack permission.
MITRE ATT&CK classifications are stored on the platform as a built-in taxonomy that is only accessible through the Create ATT&CK classification modal.
The read attack permission allows access to this built-in taxonomy. With this and modify entities permissions, users can add ATT&CK classifications to entities.
Entities and observables
You can see MITRE ATT&CK classifications assigned to an entity when you open these in the entity builder:
An entity with an ATT&CK classification
An entity or observable related to an entity with an ATT&CK classification
Only entities can be assigned ATT&CK classifications.
ATT&CK classifications appear in the following tabs of the entity builder:
Overview tab
Entities have a MITRE ATT&CK field in the entity builder OVERVIEW tab. This field allows you to add and remove ATT&CK classifications assigned to it.
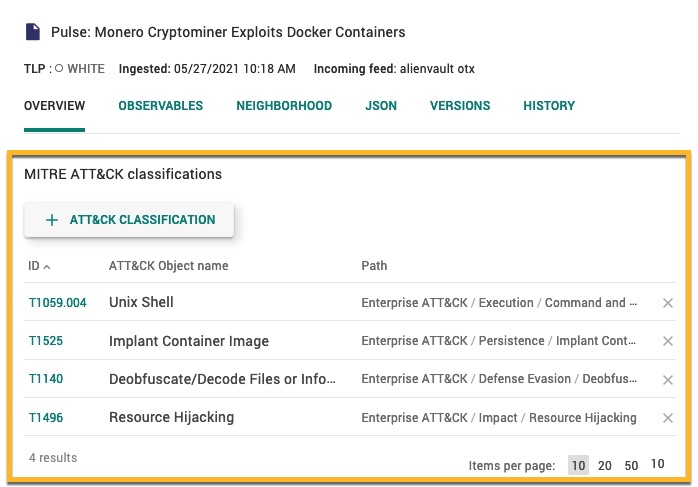
MITRE ATT&CK classifications are not displayed when you Edit an entity. They are only visible in the entity OVERVIEW tab.
Neighborhood tab
You can also see the ATT&CK classifications assigned to a related entity in the NEIGHBORHOOD tab when viewing entities and observables.
ATT&CK classifications appear in two sections under the NEIGHBORHOOD tab:
Directly related entities
MITRE ATT&CK classifications of entities on the graph
The Directly related entities section displays ATT&CK IDs for related entities that have ATT&CK classifications in the ATT&CK IDs column.
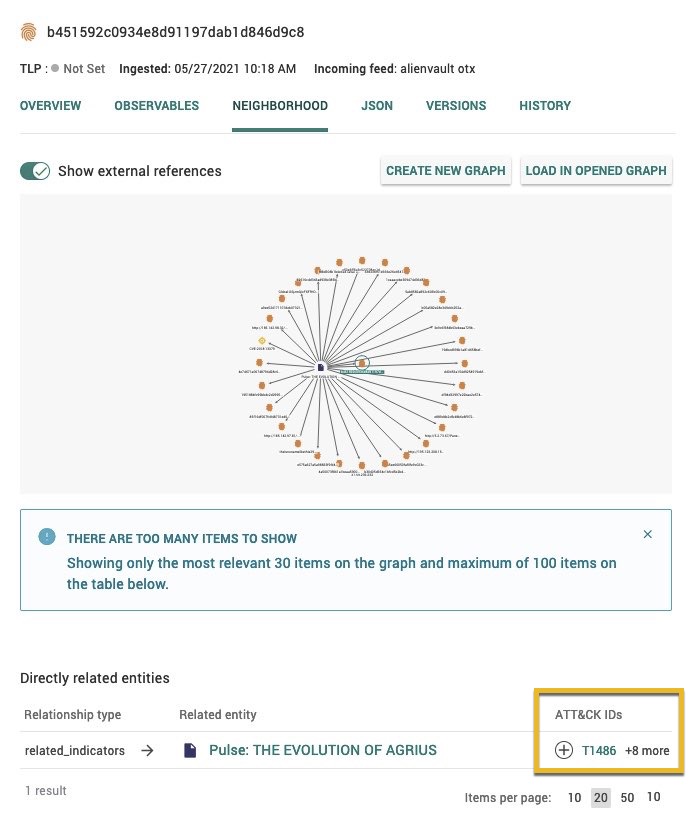
Here, you can:
Select the add icon (
 ) to add and remove ATT&CK classifications for that related entity.
) to add and remove ATT&CK classifications for that related entity.Select the ATT&CK ID (e.g., T1059.004) to display a description of that ATT&CK classification.
The MITRE ATT&CK classifications of entities on the graph section displays a table of entities in the current entity or observable’s neighborhood graph that have ATT&CK classifications:
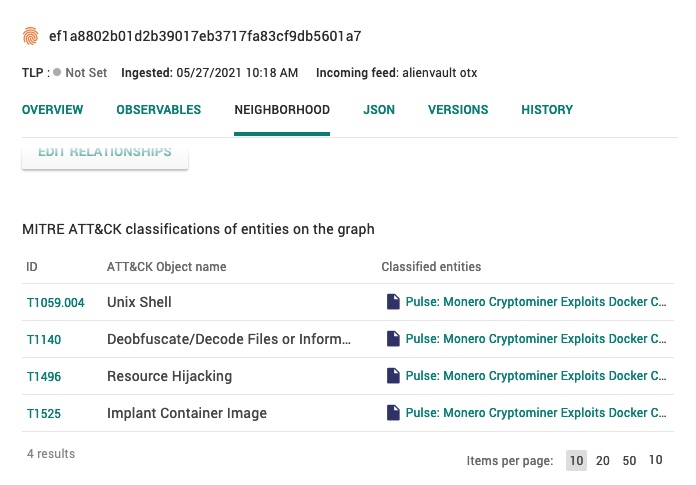
Here, you can:
Select the ATT&CK ID (e.g., T1059.004) to display a description of that ATT&CK classification.
Select entities in the Classified entities column to open that entity in a new modal.
Add ATT&CK classifications to entities
Select an entity to open the entity builder Overview tab.
In the Overview tab, scroll down to the MITRE ATT&CK classifications section.
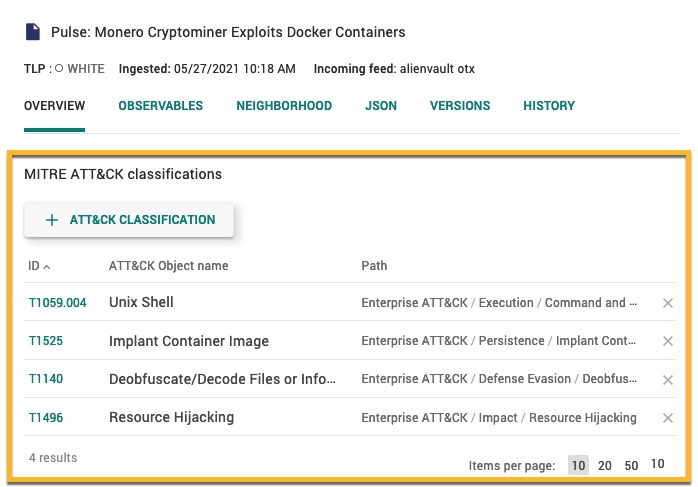
Select + ATT&CK CLASSIFICATION.
In the Create ATT&CK classification modal that appears, select the drop-down menu.
Start typing to filter the entries in the drop-down menu, and select one or more classifications.
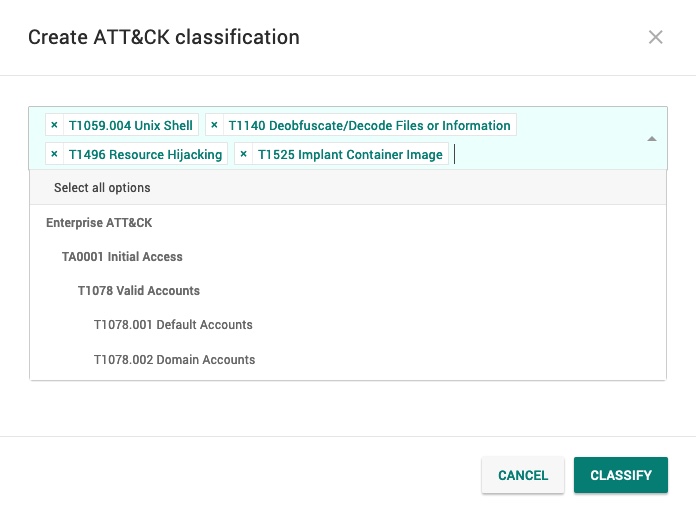
Select CLASSIFY to save your changes.
When selecting ATT&CK classifications in Create ATT&CK classification, you can hover over the information icon (
) to display information about that ATT&CK classification.
Select READ MORE to go to the page for that classification on https://attack.mitre.org/.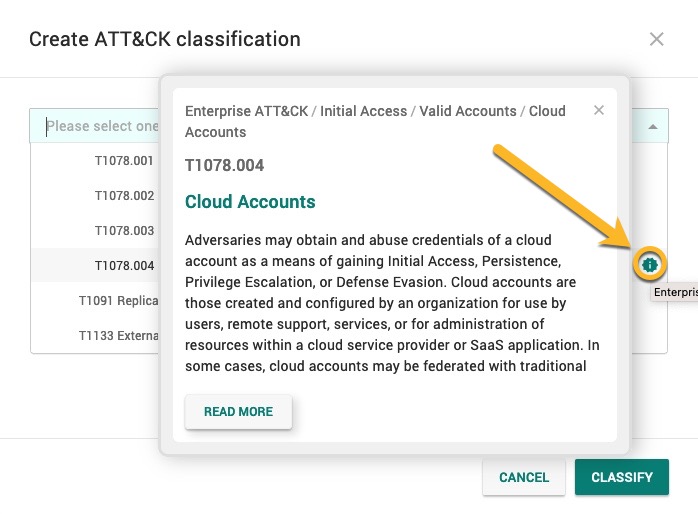
Browse by ATT&CK classification
When viewing entities in Search ( ) > GO TO SEARCH AND BROWSE > Entities, you can:
) > GO TO SEARCH AND BROWSE > Entities, you can:
Display ATT&CK classifications for results
Filter results by ATT&CK classification
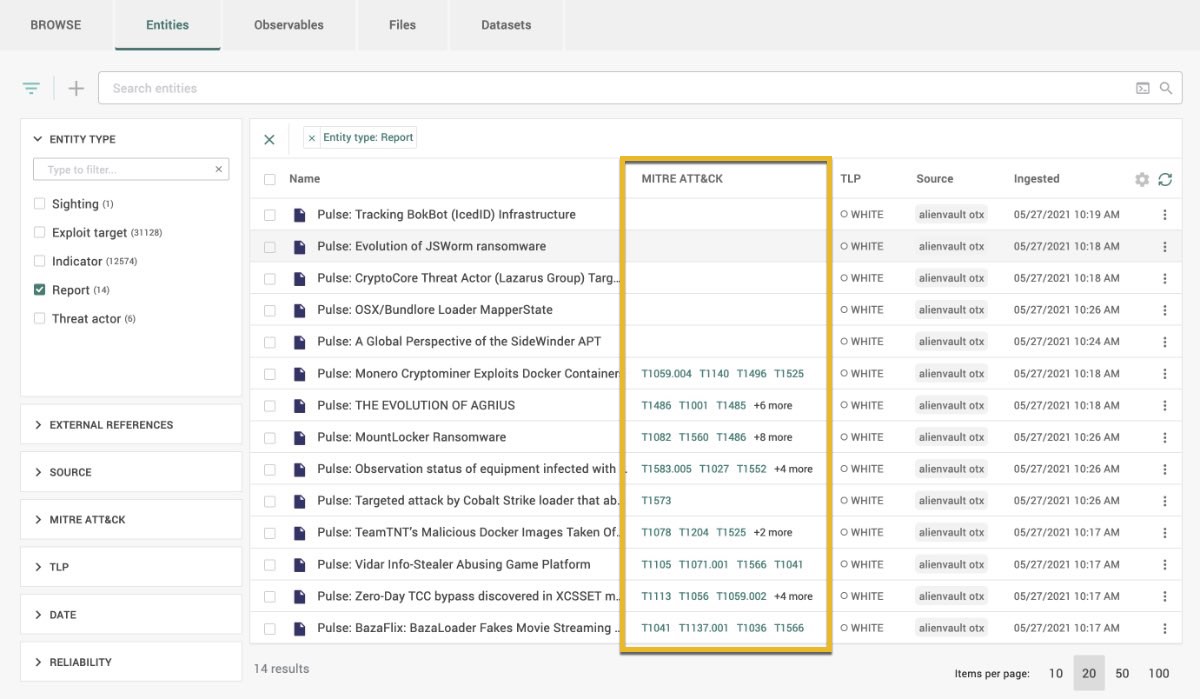
If the MITRE ATT&CK column is not visible, you can set the Intelligence Center to display it:
On the right of the table of search results, select the Settings icon (
 ).
).
In the Customize list columns modal that appears, select MITRE ATT&CK.
Select SAVE.
You can filter results by ATT&CK classification in BROWSE > Entities by:
Selecting Filter (
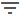 ) in the top left.
) in the top left.Select the MITRE ATT&CK section to expand it.
Start typing to search for an ATT&CK classification.
Select one or more ATT&CK classifications from the list to filter results by.
Search by ATT&CK classification
You can search for entities that have ATT&CK classifications by searching the Intelligence Center with these queries:
|
Query |
Description |
|
meta.attack.id: <ATT&CK_ID> |
Retrieves entities classified with that ATT&CK ID. For the possible ways to write <ATT&CK_ID>, see the table below. For example: Retrieves all entities that are classified with technique T1001. |
|
meta.attack.name: <string> |
Retrieves entities whose assigned ATT&CK classifications contains <string> in their names. For example: Retrieves all entities that have ATT&CK classifications with names that contain “encryption”, such as techniques “T1573 Encrypted Channel” and “T1486 Data Encrypted for Impact”. |
<ATT&CK_ID> can be written in these ways:
|
Syntax |
Example |
|
<TACTIC_ID> |
TA0042 |
|
<TECHNIQUE_ID> |
T1583 |
|
<TECHNIQUE_ID>.<SUBTECHNIQUE_ID> |
T1583.005 |
|
<TACTIC_ID>:<TECHNIQUE_ID>.<SUBTECHNIQUE_ID> |
TA0042:T1583.005 |
Analyze ATT&CK data in a graph
MITRE ATT&CK data can be visualized in the Intelligence Center's graph. See the Graph section for information about adding entities to a graph and analyzing them.
Enable MITRE ATT&CK data in a graph
To enable MITRE ATT&CK data in a graph, select ATT&CK on the top navigation bar. This displays the technique and the number of MITRE ATT&CK objects associated with the entity.
To remove the ATT&CK objects from the graph, select and toggle ATT&CK.
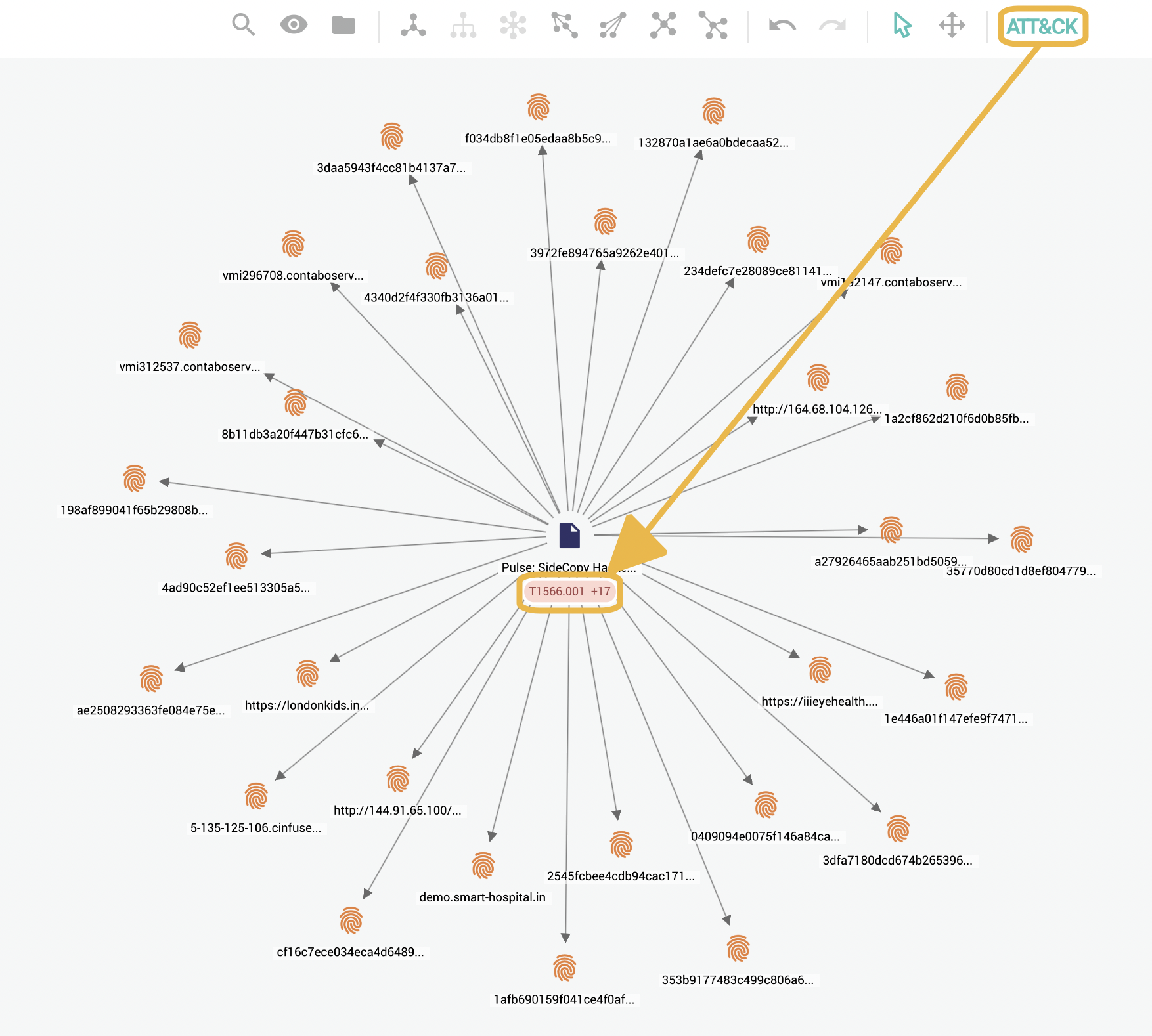
Display MITRE ATT&CK techniques as nodes
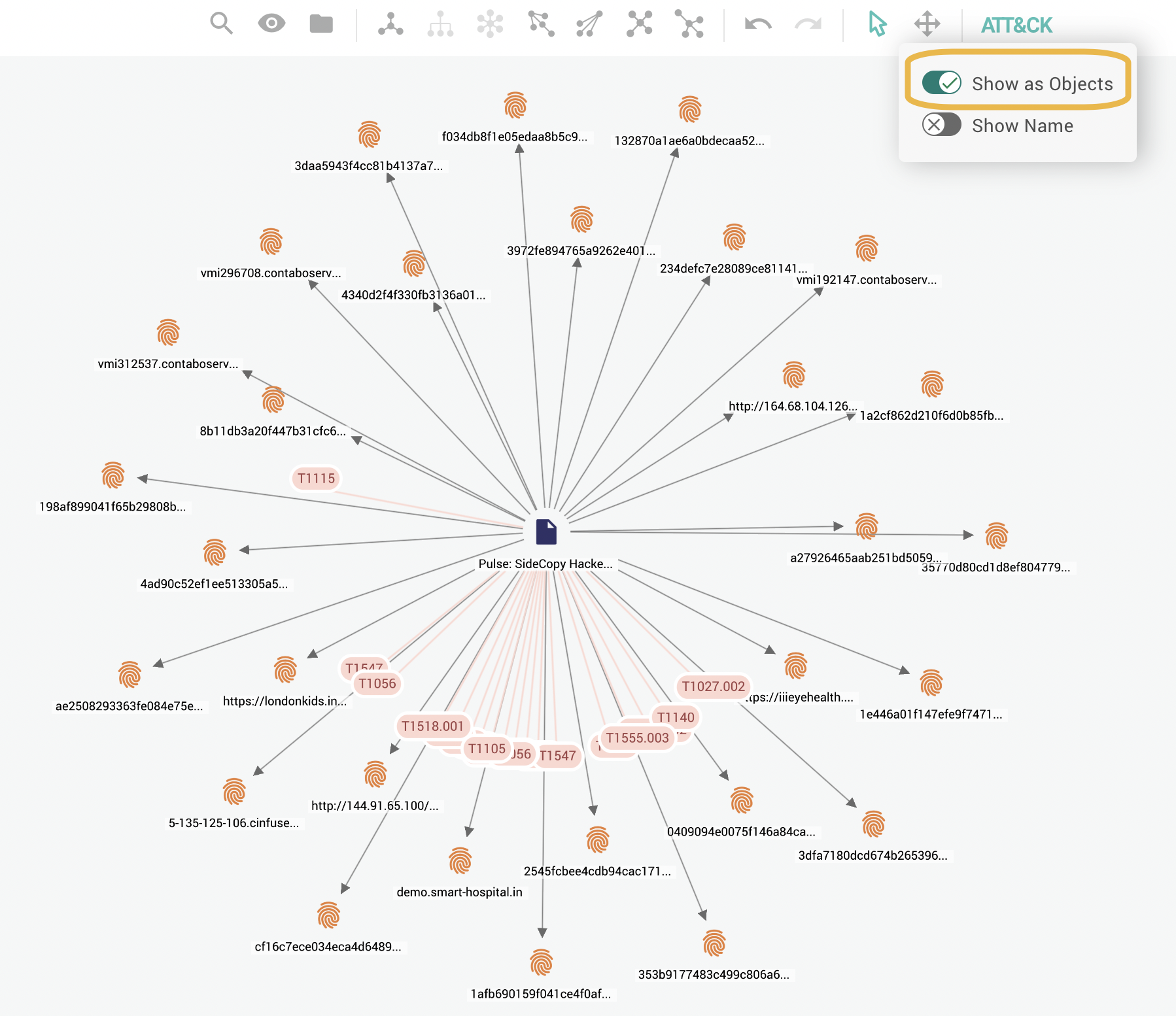
To display all the associated MITRE ATT&CK techniques and sub-techniques as nodes with IDs, select ATT&CK > Show as Objects on the top navigation bar.
Display MITRE ATT&CK names
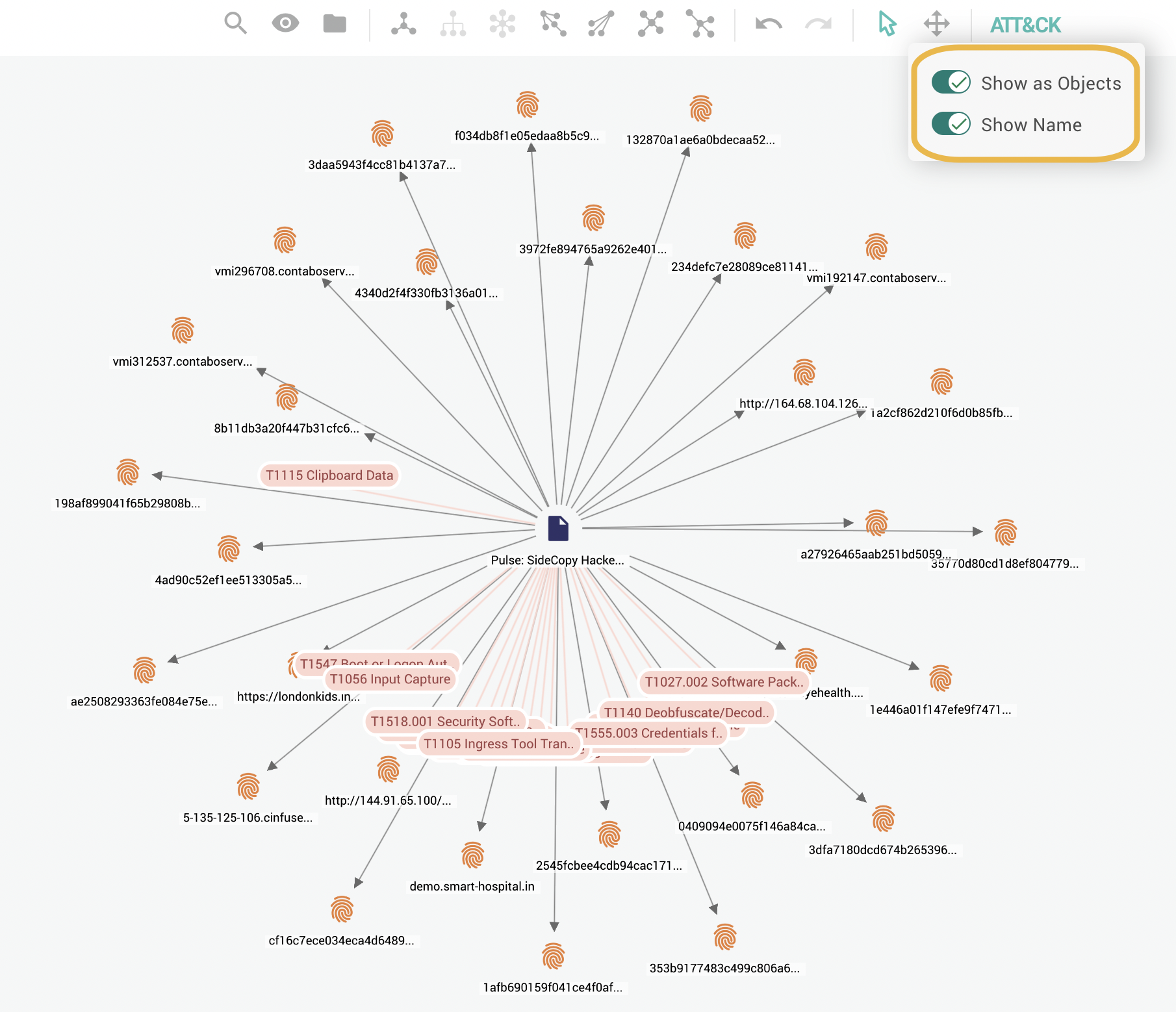
To display all the associated MITRE ATT&CK techniques and sub-techniques as nodes with IDs and their names that provide basic information about the technique, select ATT&CK > Show Name on the top navigation bar. Show as Objects must also be enabled to see individual ATTA&CK objects.
Display information about a MITRE ATT&CK classification
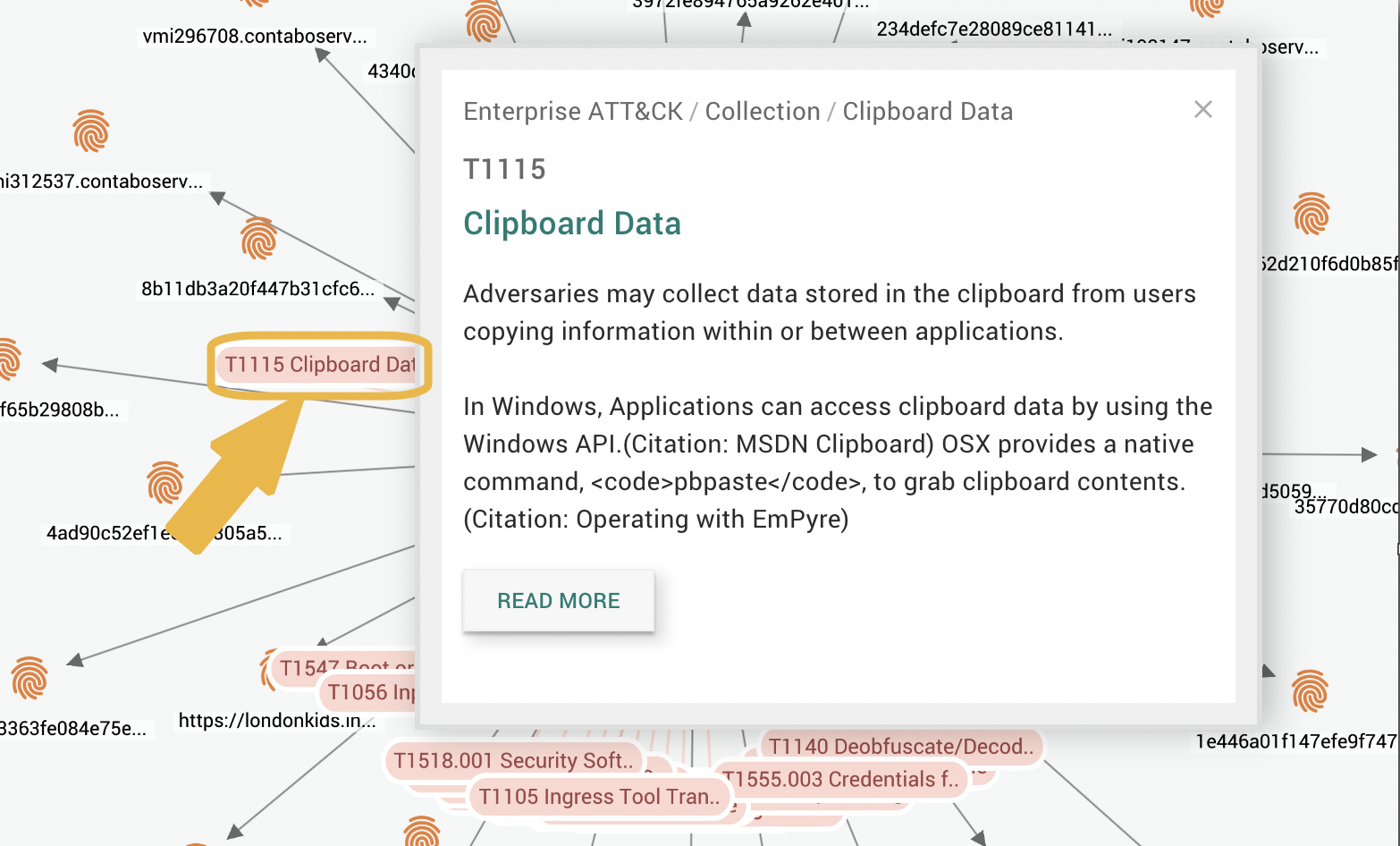
To see more information about an ATT&CK object in the graph, click and select the object to display a popup.
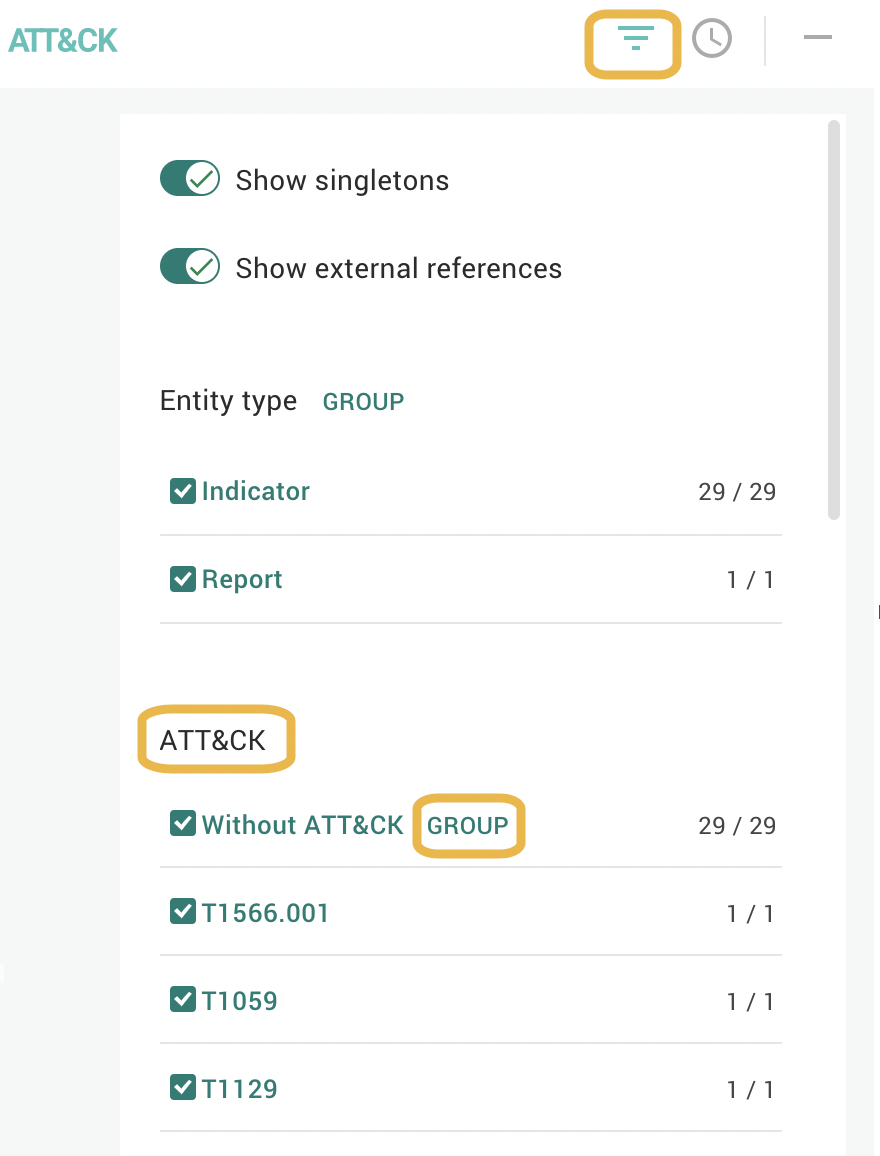
Filter and group MITRE ATT&CK objects
To filter and view specific ATT&CK objects based on their IDs, go to Filter ( ) on the top navigation bar and then select or unselect the required ATT&CK IDs under ATT&CK.
) on the top navigation bar and then select or unselect the required ATT&CK IDs under ATT&CK.
To group ATT&CK objects, select GROUP against the ATT&CK objects. See the Groups page for more information on grouping entities in a graph.
Export entities
Only the EclecticIQ JSON export format supports ATT&CK classifications.
When exporting to JSON, the ATT&CK classifications appear in the meta.attack field of the resulting JSON object:
{
"content-type": "urn:eclecticiq.com:json:1.0",
"enrichments": [],
"entities": [
// Other entities
{
"attachments": [],
"data": {
// Data for this entity
},
"enrichment_extracts": [],
"external_url": "https://platform.example.com/entity/8629ca97-9cc0-4974-9d4b-a4e56b734ca4",
"extracts": [
// Observables
],
"id": "8629ca97-9cc0-4974-9d4b-a4e56b734ca4",
"meta": {
"attack": [
{
"id": "TA0040:T1486",
"name": "Data Encrypted for Impact"
},
{
"id": "TA0011:T1001",
"name": "Data Obfuscation"
},
{
"id": "TA0040:T1485",
"name": "Data Destruction"
},
{
"id": "TA0001:T1190",
"name": "Exploit Public-Facing Application"
},
{
"id": "TA0003:T1505",
"name": "Server Software Component"
},
{
"id": "TA0002:T1072",
"name": "Software Deployment Tools"
},
{
"id": "TA0008:T1072",
"name": "Software Deployment Tools"
},
{
"id": "TA0002:T1059",
"name": "Command and Scripting Interpreter"
},
{
"id": "TA0011:T1090",
"name": "Proxy"
},
{
"id": "TA0042:T1583.005",
"name": "Botnet"
}
],
// Other metadata for this entity
"title": "TITLE OF REPORT",
"tlp_color": "WHITE"
},
"relevancy": 0.9516951530106196,
"sources": [
{
"name": "Feed name",
"source_id": "4e72f561-1c28-457a-a625-2ec9f40c87d1",
"source_type": "incoming_feed"
}
]
},
// Other entities
],
"entity_counts": {
"relation": 78,
"report": 1
},
"outgoing_feed_name": "Exported Entities",
"platform-version": "2.10.0",
"timestamp": "2021-06-07T12:28:39.993744+00:00"
}Known limitations
Enterprise ATT&CK
The Intelligence Center only has Enterprise ATT&CK classifications built into the Intelligence Center.
You cannot add to these built-in ATT&CK classifications on the Intelligence Center, or change them.
Assign techniques with ambiguous tactics
ATT&CK techniques and sub-techniques may belong to more than one tactic.
For example, the MITRE ATT&CK data model allows you to classify a threat actor with the technique “T1072 Software Deployment Tools”. However, T1072 occurs in both “TA0002 Execution” and “TA0008 Lateral Movement” tactics. The ATT&CK model does not require you to specify a tactic for an observed technique or sub-technique. This allows for analysts to map data to ATT&CK where techniques or sub-techniques can be identified, but tactics are ambiguous or unavailable.
The Intelligence Center does not support this ambiguity. All ATT&CK classifications on the Intelligence Center must have a specific parent tactic.
To work around this, you can assign all possible instances of an ATT&CK classification where the parent classification is ambiguous.
For example, if an entity should be assigned T1072, but has an ambiguous parent tactic, then assign both TA0002:T1072 and TA0008:T1072 to the entity to maintain that ambiguity.