Incoming feed - NCFTA ListServ Intel
Configure the NCFTA ListServ Intel feed to ingest National Cyber-Forensics and Training Alliance (NCFTA) reports disseminated through a ListServ system.
This procedure describes how to configure incoming feeds for a particular feed data source, transport type, or content type.
For more information about configuring common options shared across all incoming feeds, see Configure incoming feeds general options.
|
|
Specifications |
|
Transport types |
National Cyber-Forensics and Training Alliance (NCFTA) |
|
Content type |
NCFTA Records JSON |
|
Ingested data |
Reports disseminated through the NCFTA ListServ lists. |
|
Processed data |
Reports, malware and malware variant TTPs, and observables, based on retrieved data. Sets relationships, where applicable, between reports, malware variants, and malware; and between reports and observables. |
|
Description |
NCFTA ListServ Intel CyFin reports (default list) focus on cyber threats to the financial services industry, such as spam-based fraud and money laundering. The reports target financial services threats and incidents carried out especially through botnets, malware, phishing, and social engineering. |
Prerequisites
Users need an API key to configure the NCFTA ListServ Intel API service.
If necessary, contact the intelligence provider to subscribe to the service and to obtain this information, along with any required authentication and authorization credentials.
Limitations
The extension relies on the NCFTA ListServ Intel API service.
Therefore, it inherits any access limitations the API service enforces.
Configure the incoming feed
Create or edit an incoming feed.
From the Transport type drop-down menu, select National Cyber-Forensics and Training Alliance (NCFTA).
From the Content type drop-down menu, select NCFTA Records JSON.
The API URL field is prepopulated with the default URL to access the API service.
Default value: https://listservintel.ncfta.net/In the API key field, enter your NCFTA ListServ Intel API key.
In the List name field, enter the name of the NCFTA ListServ list you want to retrieve records from.
Default value: cyfinTo check the validity of the server-side SSL certificate when sending requests, select SSL verification.
To validate a self-signed or a privately signed certificate, enter the full path to the CA bundle in Path to SSL certificate file.
Allowed formats:.ca-bundle
.pem
To store your changes, click Save; to discard them, click Cancel.
Ingestion and processing
|
Ingested data |
Resulting output |
|
Report |
Entities and observables extracted from the ingested NCFTA ListServ Intel reports:
|
Reports
Resulting reports are prepopulated with the following details:
Title is populated with NCFTA Report - ${NCFTA report ID}
Summary is populated with content from the comments in the retrieved NCFTA records, if any.
Analysis is populated with content from the following fields in the retrieved NCFTA records, where available:
Bank account number
Bank routing number
SWIFT code
Bank name
Bank location
Bank address
Transaction amount
Number of stock shares
Stock symbol on the stock market
Social Security Number (SSN)
Email sender or API user name of the reporter of the event
Thread ID of the NCFTA ListServ email
Money transmitter name
Bitcoin address of the threat actors
Arrival date
Departure date
Company name
Date of birth
Email address(es)
Name
Phone
User name
Device fingerprint
Web browser user agent
Web browser cookie
Protocol used to transport the malware data
Intent is set to Threat report.
Identity is set to NCFTA ListServ Intel.
Roles is set to Initial Author.
References is populated with https://listservintel.ncfta.net/api/fetch/
The Estimated observed time corresponds to the timestamp in the source NCFTA record defining when the malicious activity was reported.
If this timestamp is not available in the source NCFTA record, the platform looks for the following fallback data:Either the timestamp defining when the malicious activity took place.
Or the timestamp defining when the record was added to the NCFTA database.
The Estimated threat start time corresponds to the timestamp in the source NCFTA record defining when the malicious activity took place.
If this timestamp is not available in the source NCFTA record, the platform looks for the following fallback data:Either the timestamp defining when the malicious activity was reported.
Or the timestamp defining when the record was added to the NCFTA database.
Malware TTPs
If the ingested NCFTA records contain information about malware, the platform produces malware TTPs.
Resulting malware TTPs are prepopulated with the following details:
Title is populated with Malware - ${malware name in the NCFTA record} or Malware Variant - ${malware name in the NCFTA record}
Identity is set to NCFTA ListServ Intel.
Roles is set to Initial Author.
References is populated with https://listservintel.ncfta.net/api/fetch/
Characteristics > Characteristic is set to Malware.
Malware > Name is populated with the name of the malware as retrieved from the NCFTA record.
Malware > Type is populated with malware-instance.
Relationships
Resulting relationships are created between:
Reports, malware variants, and malware.
Reports and extracted observables.
Graph
After processing, an ingested NCFTA record produces a report that can be related to observables and TTPs in a way that may look similar to the following example:
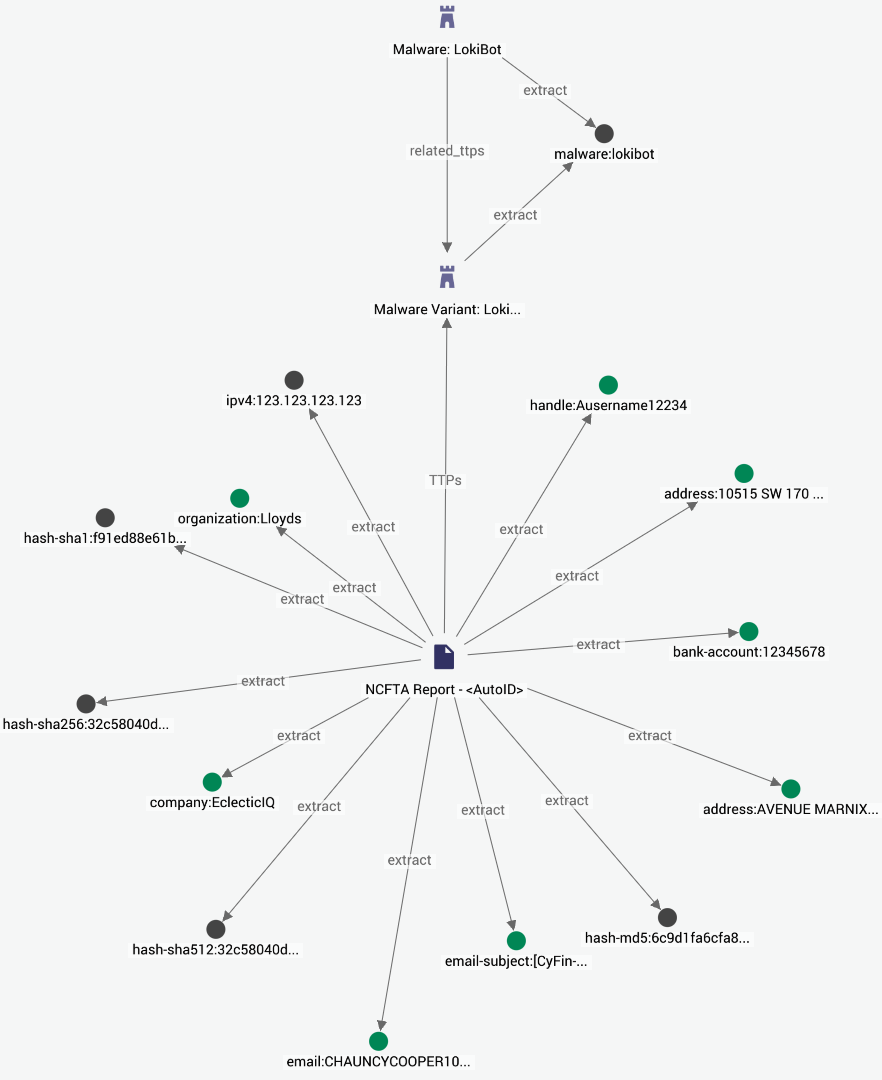
An ingested NCFTA record produces a report that can be related to observables and TTPs in a way that may look similar to this example
Test the feed
In the top navigation bar, click Data Configuration > Incoming feeds.
Click the feed that you just created, using the steps above.
In the Overview view, click Download now.
Click Ingested entities and check that entities have been ingested into the platform.
Or:
In the top navigation bar, click Intelligence > All intelligence > Browse.
Click the Entities tab.
In the top-left corner, click
.
From the Source drop-down menu, select the incoming feed you have just created, using the steps.
You can also filter also by entity type: from the Entity drop-down menu, select the entity types you want to include in the filtered results.