Set up LDAP
Configure LDAP sign-in to delegate Intelligence Center user authentication to an external authentication mechanism.
Configure LDAP authentication
You can configure the Intelligence Center to import users and groups from an LDAP directory service:
The LDAP service provides user and group authentication data.
Upon successfully authenticating, the Intelligence Center issues a JWT token.
Tokens are automatically refreshed every 60 seconds.
The token header contains an issued-at timestamp, which is used to check token validity.
It is preferable not to mix LDAP users and local users in the Intelligence Center.
If you create local users in the Intelligence Center, and then import LDAP users:
Imported LDAP users override the local ones.
LDAP settings override local settings when they refer to the same user.
Therefore, if you implement authentication through LDAP, it is advisable to delegate user access right management entirely to the LDAP service.
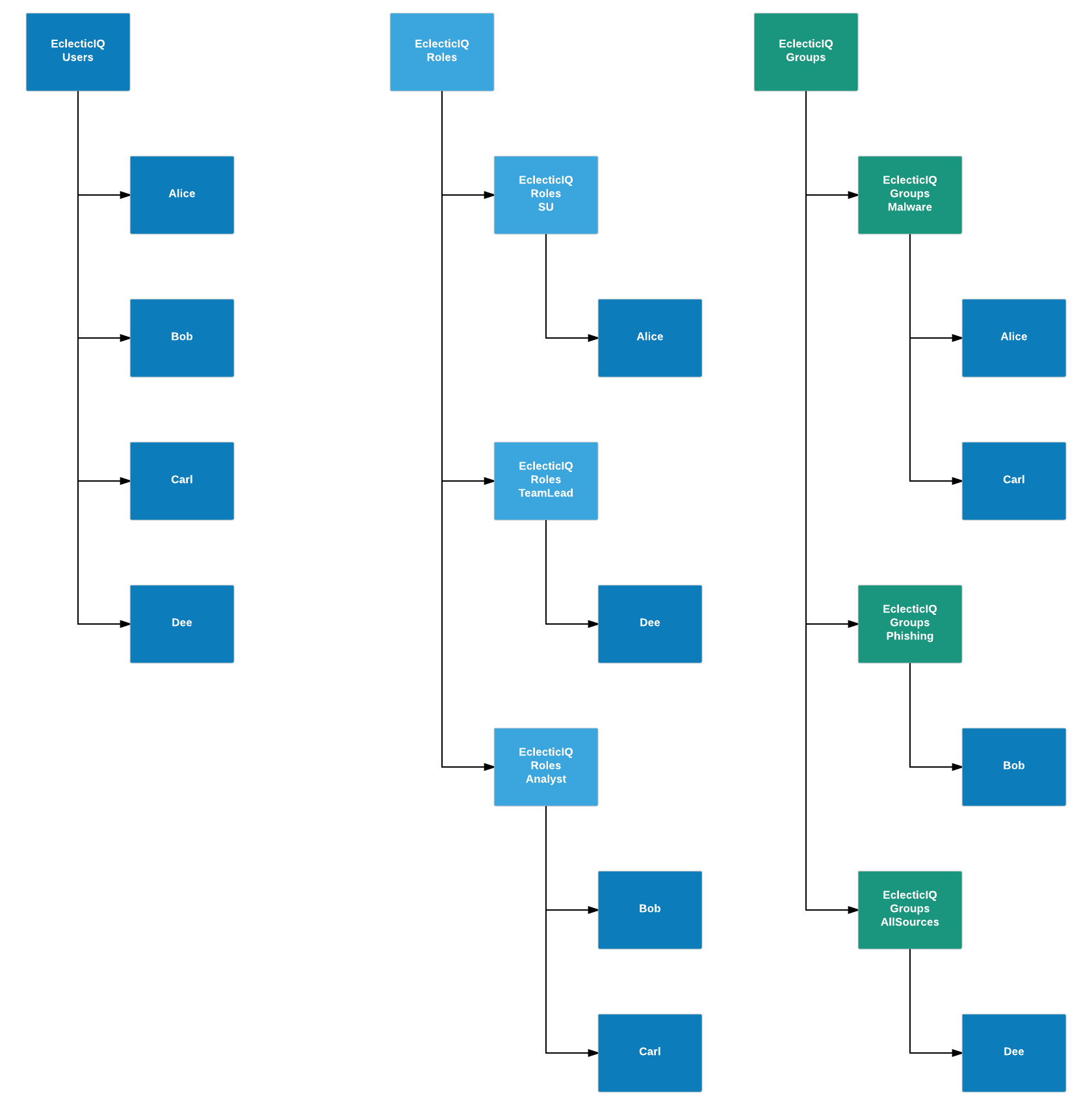
A standard way to structure LDAP groups can include the following steps:
Create an LDAP group to hold groups, an LDAP group to hold users, and an LDAP group to hold roles.
Apply some basic standard naming rules for these LDAP groups.
For example, use a prefix such as EclecticIQ or EIQ.
Example:
EclecticIQUsers
EclecticIQRoles
EclecticIQGroups
Create LDAP users as necessary.
Assign these users to the EclecticIQUsers LDAP group.
Create LDAP roles as necessary.
The role names you define in the LDAP structure should match exactly the existing role names in the Intelligence Center.
Assign these roles to the EclecticIQRoles LDAP group.
Create LDAP groups as necessary.
The group names you define in the LDAP structure should match exactly any existing group names in the Intelligence Center.
Assign these groups to the EclecticIQGroups LDAP group.
To define user group membership and user access policies, add the users to the child groups and the child roles of the EclecticIQGroups and EclecticIQRoles parent groups.
To configure LDAP authentication:
Append the following attributes and set them to the appropriate values for your environment in the /etc/eclecticiq/platform_settings.py file.
Ensure you represent Intelligence Center roles and groups as LDAP groups.
LDAP role and group names, that is, the values of the LDAP_ROLE_NAME_ATTR and LDAP_GROUP_NAME_ATTR attributes, should exactly match the corresponding role and group name values in the Intelligence Center.
LDAP_AUTH_ENABLED: Boolean switch to enable/disable LDAP authentication.
Default value: False (LDAP disabled).
To enable LDAP authentication, set it to True.
LDAP_URI: URI pointing to the designated LDAP instance. It supports ldap://, as well as ldaps://protocols.
Example:
LDAP_URI = "ldap://ldap.example.com"
LDAP_IGNORE_TLS_ERRORS: Boolean switch to enable/disable TLS error checking such as invalid certificates, chain validation issues, and so on.
Default value: True (TLS errors are ignored).
LDAP_BIND_DN: specify the valid credentials to bind to the LDAP connection, search for users, read groups and roles.
LDAP_BIND_PASSWORD: specify the password associated with the binding credentials.
Example:
LDAP_BIND_DN = "cn=Manager,dc=ldap,dc=eclecticiq" LDAP_BIND_PASSWORD = "adminpassword"LDAP_USERS_FILTER: base and filter values used to search for user accounts.
The { username } placeholder value is replaced with an assigned user name.
Example:
LDAP_USERS_FILTER = ( "ou=EclecticIQUsers,dc=ldap,dc=eclecticiq", "(uid={username})")LDAP_GROUPS_FILTER: base and filter values used to search for user groups.
The { username } placeholder value is replaced with an assigned user group name.
Example:
LDAP_GROUPS_FILTER = ( "ou=EclecticIQGroups,dc=ldap,dc=eclecticiq", "(&(memberUid={username})(objectClass=posixGroup))")LDAP_ROLES_FILTER: base and filter values used to search for user roles.
The { username } placeholder value is replaced with an assigned role name.
Example:
LDAP_ROLES_FILTER = ( "ou=EclecticIQRoles,dc=ldap,dc=eclecticiq", "(&(memberUid={username})(objectClass=posixGroup))")LDAP_USER_FIRSTNAME_ATTR: define the naming attribute used to extract a user’s first/given name.
LDAP_USER_LASTNAME_ATTR: define the naming attribute used to extract a user’s surname/family name.
LDAP_USER_EMAIL_ATTR: define the naming attribute used to extract a user’s email address.
LDAP_ROLE_NAME_ATTR: define the naming attribute used to extract a user’s role details.
LDAP_GROUP_NAME_ATTR: define the naming attribute used to extract a user’s group details.
LDAP_USER_IS_ADMIN_ATTR: specify if the user should be granted admin rights.
Alternatively, you can grant a user admin rights by assigning them to the admin group whose name is specified in LDAP_ADMIN_ROLE_GROUP_NAME.
To grant a user admin rights, assign LDAP_USER_IS_ADMIN_ATTR the following value: “isEclecticIQAdmin”.
Example:
LDAP_USER_IS_ADMIN_ATTR = "isEclecticIQAdmin"LDAP_ADMIN_ROLE_GROUP_NAME: to grant a user admin rights, assign them to the admin group whose name is specified in LDAP_ADMIN_ROLE_GROUP_NAME.
For example, if you assign the attribute the “EclecticIQAdminsGroup” value, you can grant a user admin rights by assigning them to the EclecticIQAdminsGroup group.
Alternatively, you can grant a user admin rights by assigning them the “isEclecticIQAdmin” value defined in LDAP_USER_IS_ADMIN_ATTR.
Example:
LDAP_ADMIN_ROLE_GROUP_NAME = "EclecticIQAdminsGroup"
LDAP referrals are not supported.
Example LDAP configuration
LDAP_AUTH_ENABLED = FalseLDAP_URI = "ldaps://toolbox.iw"LDAP_IGNORE_TLS_ERRORS = TrueLDAP_BIND_DN = "cn=Manager,dc=ldap,dc=eclecticiq"LDAP_BIND_PASSWORD = "adminpassword"# These are 2-tuples of the form (base, filter_template)LDAP_USERS_FILTER = ( "ou=Users,dc=ldap,dc=eclecticiq", # Base "(uid={username})", # Filter template)LDAP_GROUPS_FILTER = ( "ou=EclecticIQGroups,dc=ldap,dc=eclecticiq", "(&(memberUid={username})(objectClass=posixGroup))",)LDAP_ROLES_FILTER = ( "ou=EclecticIQRoles,dc=ldap,dc=eclecticiq", "(&(memberUid={username})(objectClass=posixGroup))",)LDAP_USER_FIRSTNAME_ATTR = "cn"LDAP_USER_LASTNAME_ATTR = "sn"LDAP_USER_EMAIL_ATTR = "mail"LDAP_ROLE_NAME_ATTR = "cn"LDAP_GROUP_NAME_ATTR = "cn"LDAP_CASE_SENSITIVE_MATCHING = TrueLDAP_USER_IS_ADMIN_ATTR = "isEclecticIQAdmin"